41
network. You can configure the firewall to allow specific application traffic from the Internet to pass
through to a computer on your local network.
If the firewall has been configured to allow traffic from the Internet to pass through, the device and the
allowed application are listed. If application traffic is allowed, external users on the Internet can have
limited access to your local network. This access might be required in order for some programs such as
game servers and messaging software to operate properly. For example, a remote game player on the
Internet might need to contact the game server program that you have installed on your local network in
order to play against you. Normally, the firewall blocks this communication. By changing the firewall
settings, this communication is permitted to pass through a “pinhole” in the firewall. This function may be
referred to as “port-mapping” or “port-forwarding” in your software program documentation.
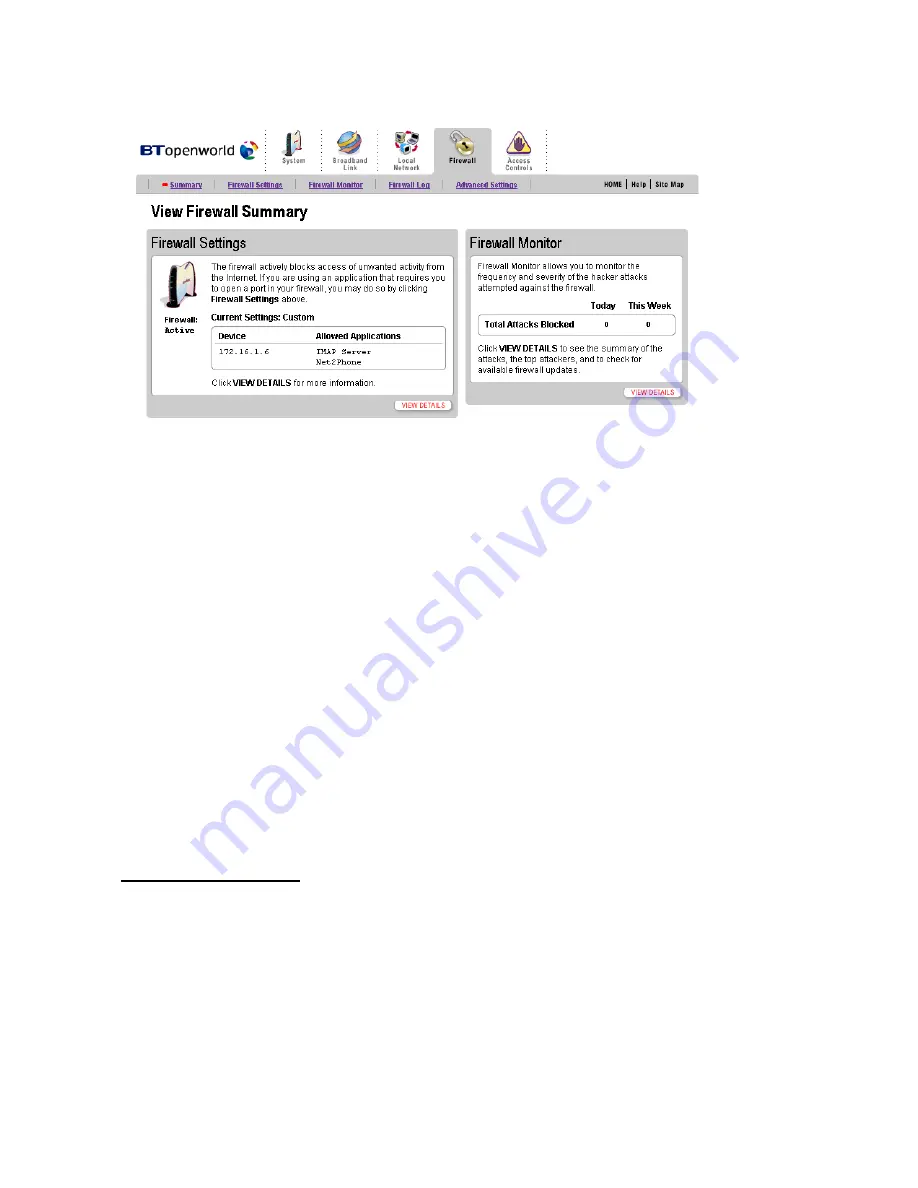
A status message displays the firewall’s Current Settings. The default settings disallow all unsolicited
inbound traffic to provide maximum protection for your local network. The Current Settings will be
displayed as “Custom” if any applications have been associated with computers on your network.
The summary displays an access list showing the computers (“Devices”) on your network and the names of
the Allowed Applications for each computer.
Click
VIEW DETAILS
to access the Firewall Details page, which shows a list of all the devices that have
applications configured in the firewall and the details of these configurations.
Viewing firewall details
The Firewall Details page displays the details of all the applications allowed to pass through the firewall,
and includes the following information:
•
Application Type.
A special set of rules required by complex applications to ensure that all of the
necessary data is passed correctly through the firewall.
•
Protocol.
The Internet protocol used by the application to send and receive data. Data that is
transferred over the Internet must conform to one of a number of defined standards. This column
indicates the protocol used by the data for the firewall to properly forward the data to the assigned
computer. An application may require multiple protocols to communicate.
•
Port Numbers.
Some Internet protocols transfer data through specific channels or connection
numbers known as ports. For example, an instant messenger application may send a message using
















































