164
C
HAPTER
8: D
EFINING
WLAN
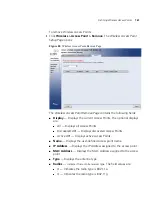
level as a wired LAN. WEP encrypts data over radio waves during
the packet transmission. WEP keys are 40 bit or 104 bit encryption
keys.
■
WPA-PSK
— Indicates that
Wi-Fi Protected Access
(WPA) is the
selected WLAN security method. WPA is based on WEP, but
provides enhanced encryption using
Temporal Key Integrity
Protocol
(TKIP). In addition, WPA improves authentication using
EAP. EAP ensures that only authorized network users access the
network though secure encryption systems.
■
WPA2-PSK
— Indicates that WPA2-PSK is the selected WLAN
security method. WPA2-PSK improves system security by
encrypting signals at a higher bit rates.
■
Passphrase/Key
— Indicates the encryption key type.
2
Define the fields.
3
Click
. The Wireless Configuration is saved at the end of the
wizard setup, and the device is updated.
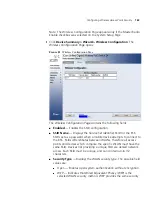
Defining Wireless
Rogue Handling
Access points are constantly scanning wireless channels. Scanning occurs
while WLAN stations are being serviced. The WLAN rogue contains
information for viewing WLAN rogue statistics. Access points then report
the discovered neighbors to the system. The system filters the
information and looks for rogue neighbors or known SSIDs. Access points
are considered rouges if: An issue occurs in the security configuration.
The access point is located in an Ad-hoc network.
A
Organizationally Unique Identifier
(OUI) is detected in the rogue BSSID.
WLAN rogues can cause disrupt WLAN service, in addition, stations which
are connected to the rogue AP are disconnected.
Summary of Contents for 3CRUS2475 24
Page 137: ...Defining LAG Membership 137...
Page 139: ...139 Defining Voice VLAN Defining GVRP...
Page 194: ...194 CHAPTER 9 CONFIGURING IP INFORMATION Static Indicates the ARP entry is a static entry...
Page 197: ...Defining ARP Interface Settings 197 Unchecked Maintains the current ARP entries...
Page 321: ...320 APPENDIX C TROUBLESHOOTING...
Page 329: ...328 APPENDIX GLOSSARY...