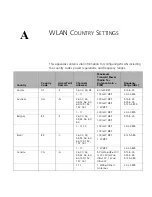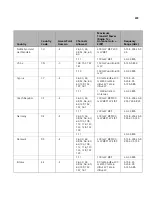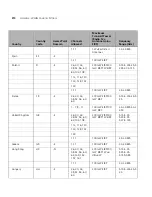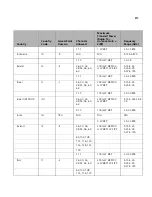
292
C
HAPTER
15: V
IEWING
S
TATISTICS
Defining RMON
Alarms
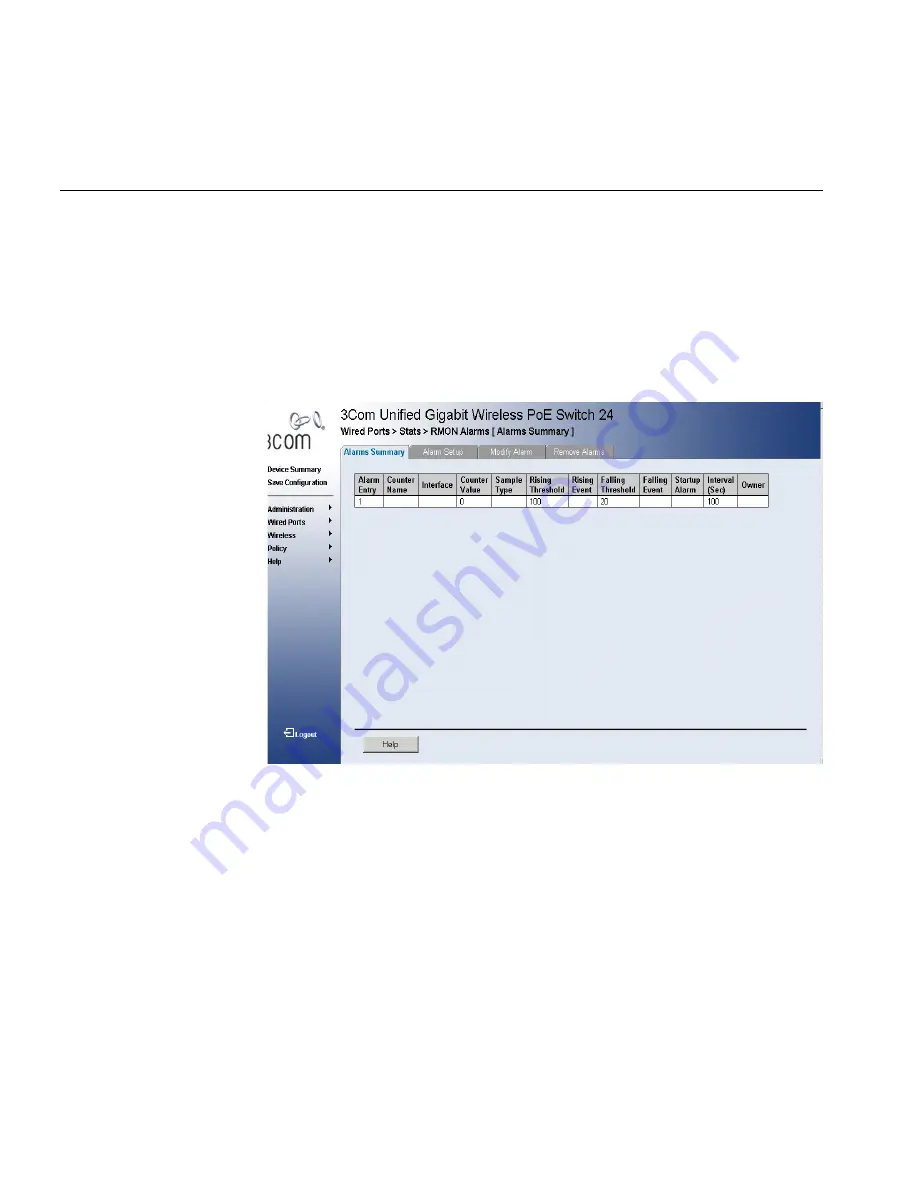
The
RMON Alarm Summary Page
contains fields for setting network
alarms. Network alarms occur when a network problem, or event, is
detected. Rising and falling thresholds generate events.
To view RMON Alarms:
1
Click
Wired Ports > Stats > RMON Alarms > Alarms Summary
. The
RMON Alarm Summary Page
opens:
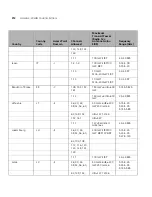
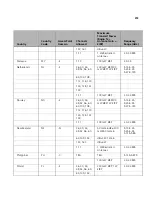
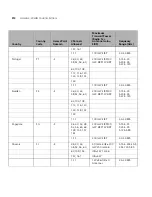
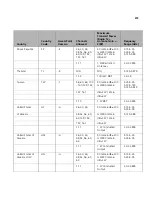
Figure 152
RMON Alarm Summary Page
The
RMON Alarm Summary Page
contains the following fields:
■
Alarm Entry
— Indicates a specific alarm.
■
Counter Name
— Displays the selected MIB variable.
■
Interface
— Displays interface for which RMON statistics are
displayed. The possible field values are:
■
Port
— Displays the RMON statistics for the selected port.
■
LAG
— Indicates LAG statistics are displayed.
■
Counter Value
— Displays the selected MIB variable value.
■
Sample Type
— Defines the sampling method for the selected
variable and comparing the value against the thresholds. The possible
field values are:
Summary of Contents for 3CRUS2475 24
Page 137: ...Defining LAG Membership 137...
Page 139: ...139 Defining Voice VLAN Defining GVRP...
Page 194: ...194 CHAPTER 9 CONFIGURING IP INFORMATION Static Indicates the ARP entry is a static entry...
Page 197: ...Defining ARP Interface Settings 197 Unchecked Maintains the current ARP entries...
Page 321: ...320 APPENDIX C TROUBLESHOOTING...
Page 329: ...328 APPENDIX GLOSSARY...