21
802.1
X
C
ONFIGURATION
Introduction to 802.1x
The 802.1x protocol (802.1x for short) was developed by IEEE802 LAN/WAN
committee to address security issues of wireless LANs. It was then used in Ethernet as
a common access control mechanism for LAN ports to address mainly authentication
and security problems.
802.1x is a port-based network access control protocol. It authenticates and controls
devices requesting for access in terms of the ports of LAN access control devices. With
the 802.1x protocol employed, a user-side device can access the LAN only when it
passes the authentication. Those failing to pass the authentication are denied when
accessing the LAN, as if they are disconnected from the LAN.
Architecture of 802.1x
Authentication
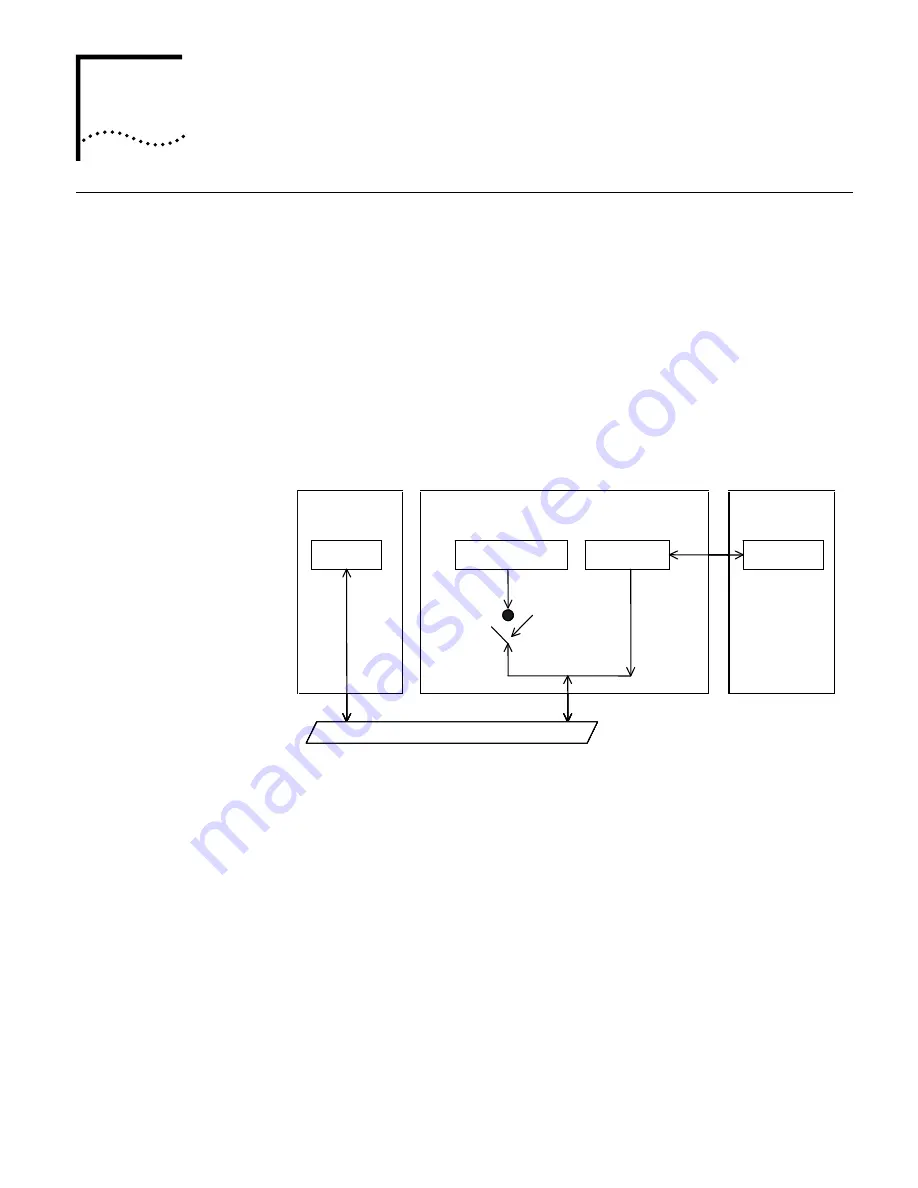
802.1x adopts a client/server architecture with three entities: a supplicant system, an
authenticator system, and an authentication server system, as shown in Figure 43.
Figure 43
Architecture of 802.1x authentication
■
The supplicant system is an entity residing at one end of the LAN segment and is
authenticated by the authenticator system connected to the other end of the LAN
segment. The supplicant system is usually a user terminal device. An 802.1x
authentication is initiated when a user launches client program on the supplicant
system. Note that the client program must support the EAPoL (extensible
authentication protocol over LANs).
■
The authenticator system authenticates the supplicant system. The authenticator
system is usually an 802.1x-supported network device (such as a S4200G series
switch). It provides the port (physical or logical) for the supplicant system to access
the LAN.
■
The authentication server system is an entity that provides authentication service
to the authenticator system. Normally in the form of a RADIUS server, the
authentication server system serves to perform AAA (authentication,
authorization, and accounting) . It also stores user information, such as user name,
password, the VLAN a user belongs to, priority, and the ACLs (access control list)
applied.
Supplicant PAE
Supplicant system
Authentication
server
Authentication
server system
Servic es pr ovided by
aut henticat or
Authenticat or PAE
Authenticator system
Port under
control
Port not authorized
Port not
Under
control
LAN/WLAN
Supplicant PAE
Supplicant system
Authentication
server
Authentication
server system
Servic es pr ovided by
aut henticat or
Authenticat or PAE
Authenticator system
Controlled port
Port not authorized
Uncontrolled
port
LAN/WLAN
Supplicant PAE
Supplicant system
Authentication
server
Authentication
server system
Servic es pr ovided by
aut henticat or
Authenticat or PAE
Authenticator system
Port under
control
Port not authorized
Port not
Under
control
LAN/WLAN
Supplicant PAE
Supplicant system
Authentication
server
Authentication
server system
Servic es pr ovided by
aut henticat or
Authenticat or PAE
Authenticator system
Controlled port
Port not authorized
Uncontrolled
port
LAN/WLAN
Summary of Contents for 4200G 12-Port
Page 10: ...8 CONTENTS...
Page 14: ...4 ABOUT THIS GUIDE...
Page 46: ...32 CHAPTER 5 LOGGING IN THROUGH WEB BASED NETWORK MANAGEMENT SYSTEM...
Page 48: ...34 CHAPTER 6 LOGGING IN THROUGH NMS...
Page 60: ...46 CHAPTER 9 VLAN CONFIGURATION...
Page 64: ...50 CHAPTER 10 MANAGEMENT VLAN CONFIGURATION...
Page 80: ...66 CHAPTER 13 GVRP CONFIGURATION...
Page 98: ...84 CHAPTER 15 LINK AGGREGATION CONFIGURATION...
Page 112: ...98 CHAPTER 18 MAC ADDRESS TABLE MANAGEMENT...
Page 126: ...112 CHAPTER 19 LOGGING IN THROUGH TELNET...
Page 162: ...148 CHAPTER 20 MSTP CONFIGURATION...
Page 274: ...260 CHAPTER 29 IGMP SNOOPING CONFIGURATION...
Page 276: ...262 CHAPTER 30 ROUTING PORT JOIN TO MULTICAST GROUP CONFIGURATION...
Page 298: ...284 CHAPTER 33 SNMP CONFIGURATION...
Page 304: ...290 CHAPTER 34 RMON CONFIGURATION...
Page 338: ...324 CHAPTER 36 SSH TERMINAL SERVICES...
Page 356: ...342 CHAPTER 38 FTP AND TFTP CONFIGURATION...
Page 365: ...Information Center Configuration Example 351 S4200G terminal logging...
Page 366: ...352 CHAPTER 39 INFORMATION CENTER...
Page 378: ...364 CHAPTER 40 BOOTROM AND HOST SOFTWARE LOADING...
Page 384: ...370 CHAPTER 41 Basic System Configuration and Debugging...
Page 388: ...374 CHAPTER 43 NETWORK CONNECTIVITY TEST...
Page 406: ...392 CHAPTER 45 CONFIGURATION OF NEWLY ADDED CLUSTER FUNCTIONS...
















































