158
C
HAPTER
21: 802.1
X
C
ONFIGURATION
■
After the maximum number of authentication retries have been made and there
are still ports that have not sent any response back, the switch will then add these
ports into the Guest VLAN.
■
When the maximum number of authentication retries is reached, the switch adds
the ports that do not return response packets to Guest VLAN.
■
Users belonging to the Guest VLAN can access the resources of the Guest VLAN
without being authenticated. But they need to be authenticated before accessing
external resources.
Normally, the Guest VLAN function is coupled with the dynamic VLAN delivery
function.
802.1x Configuration
802.1x provides a solution for authenticating users. To implement this solution, you
need to execute 802.1x-related commands. You also need to configure AAA schemes
on switches and to specify the authentication scheme (RADIUS authentication
scheme or local authentication scheme).
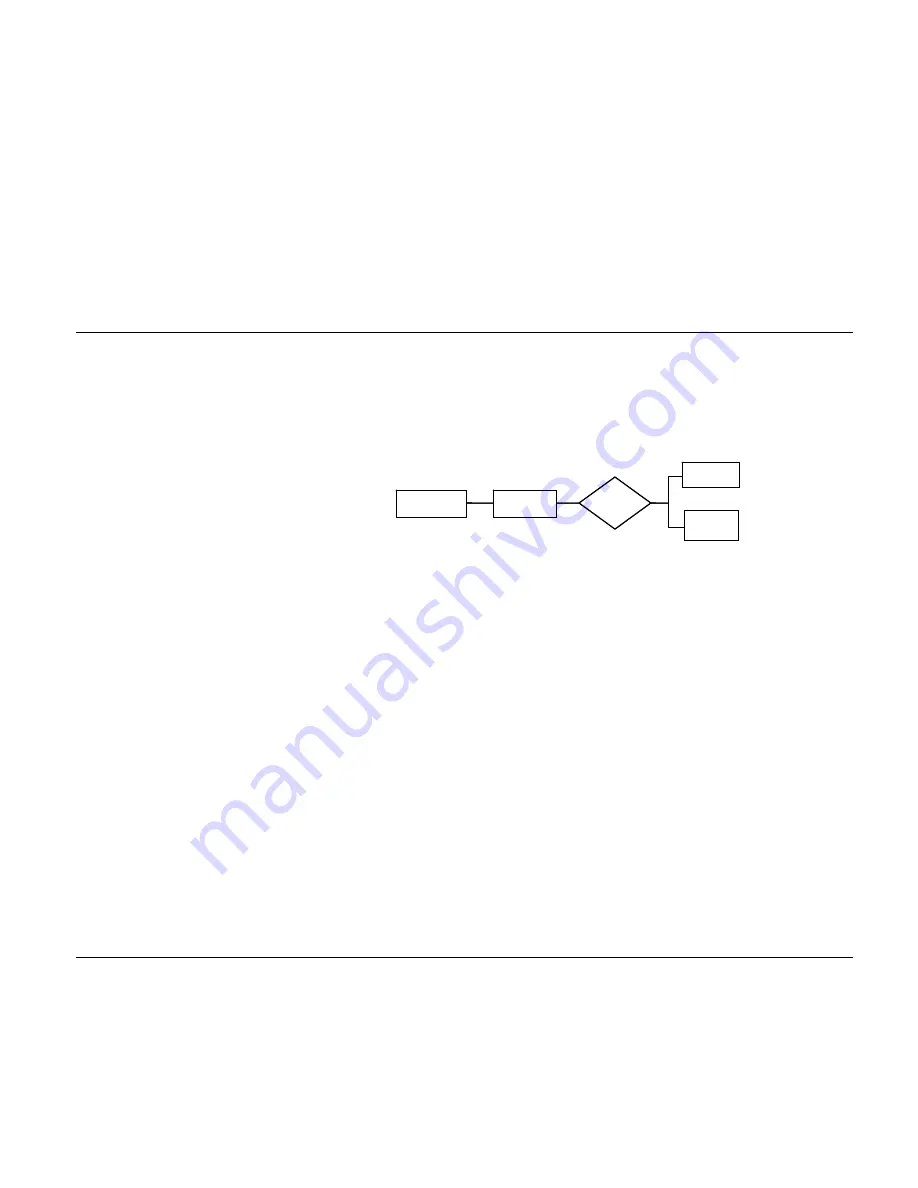
Figure 52
802.1x configuration
■
802.1x users use domain names to associate with the ISP domains configured on
switches
■
Configure the AAA scheme (a local authentication scheme or the RADIUS scheme)
to be adopted in the ISP domain.
■
If you specify to use the RADIUS scheme, that is to say the supplicant systems are
authenticated by a remote RADIUS server, you need to configure the related user
names and passwords on the RADIUS server and perform RADIUS client-related
configuration on the switches.
■
If you specify to adopt a local authentication scheme, you need to configure user
names and passwords manually on the switches. Users can pass the authentication
through 802.1x client if they provide the user names and passwords that match
with those stored in the switches.
■
You can also specify to adopt RADIUS authentication scheme, with a local
authentication scheme as a backup. In this case, the local authentication scheme is
adopted when the RADIUS server fails.
Refer to the
AAA and RADIUS Operation Manual
for detailed information about AAA
configuration.
Basic 802.1x
Configuration
To utilize 802.1x features, you need to perform basic 802.1x configuration.
Prerequisites
■
Configure ISP domain and its AAA scheme, specify the authentication scheme
(RADIUS or a local scheme) .
■
Ensure that the service type is configured as
lan-access
(by using the
service-type
command) for local authentication scheme.
ISP domain
configurati on
AAA sc heme
Local
aut henticati on
RADIUS
scheme
802.1x
configurati on
ISP domain
configurati on
AAA sc heme
Local
aut henticati on
RADIUS
scheme
802.1x
configurati on
Summary of Contents for 4200G 12-Port
Page 10: ...8 CONTENTS...
Page 14: ...4 ABOUT THIS GUIDE...
Page 46: ...32 CHAPTER 5 LOGGING IN THROUGH WEB BASED NETWORK MANAGEMENT SYSTEM...
Page 48: ...34 CHAPTER 6 LOGGING IN THROUGH NMS...
Page 60: ...46 CHAPTER 9 VLAN CONFIGURATION...
Page 64: ...50 CHAPTER 10 MANAGEMENT VLAN CONFIGURATION...
Page 80: ...66 CHAPTER 13 GVRP CONFIGURATION...
Page 98: ...84 CHAPTER 15 LINK AGGREGATION CONFIGURATION...
Page 112: ...98 CHAPTER 18 MAC ADDRESS TABLE MANAGEMENT...
Page 126: ...112 CHAPTER 19 LOGGING IN THROUGH TELNET...
Page 162: ...148 CHAPTER 20 MSTP CONFIGURATION...
Page 274: ...260 CHAPTER 29 IGMP SNOOPING CONFIGURATION...
Page 276: ...262 CHAPTER 30 ROUTING PORT JOIN TO MULTICAST GROUP CONFIGURATION...
Page 298: ...284 CHAPTER 33 SNMP CONFIGURATION...
Page 304: ...290 CHAPTER 34 RMON CONFIGURATION...
Page 338: ...324 CHAPTER 36 SSH TERMINAL SERVICES...
Page 356: ...342 CHAPTER 38 FTP AND TFTP CONFIGURATION...
Page 365: ...Information Center Configuration Example 351 S4200G terminal logging...
Page 366: ...352 CHAPTER 39 INFORMATION CENTER...
Page 378: ...364 CHAPTER 40 BOOTROM AND HOST SOFTWARE LOADING...
Page 384: ...370 CHAPTER 41 Basic System Configuration and Debugging...
Page 388: ...374 CHAPTER 43 NETWORK CONNECTIVITY TEST...
Page 406: ...392 CHAPTER 45 CONFIGURATION OF NEWLY ADDED CLUSTER FUNCTIONS...