Overview
171
2
The Identifier field (one byte) identifies the request and response packets. It is subject
to the Attribute field and varies with the received valid responses, but keeps
unchanged during retransmission.
3
The Length field (two bytes) specifies the total length of the packet (including the
Code, Identifier, Length, Authenticator and Attribute fields). The bytes beyond the
length will be regarded as padding characters and are ignored upon receiving the
packet. If the received packet is shorter than the value of this field, it will be
discarded.
4
The Authenticator field (16 bytes) is used to verify the packet returned from the
RADIUS server; it is also used in the password hiding algorithm. There are two kinds
of authenticators: Request and Response.
5
The Attribute field contains special authentication, authorization, and accounting
information to provide the configuration details of a request or response packet. This
field is represented by a field triplet (Type, Length and Value):
■
The Type field (one byte) specifies the type of the attribute. Its value ranges from 1
to 255. Table 133 lists the attributes that are commonly used in RADIUS
authentication and authorization.
■
The Length field (one byte) specifies the total length of the Attribute field in bytes
(including the Type, Length and Value fields).
■
The Value field (up to 253 bytes) contains the information about the attribute. Its
content and format are determined by the Type and Length fields.
4
Accounting-Request Direction: client->server.
The client transmits this packet to the server to request the server
to start or end the accounting (whether to start or to end the
accounting is determined by the Acct-Status-Type attribute in the
packet).
This packet carries almost the same attributes as those carried in
the Access-Request packet.
5
Accounting-Respon
se
Direction: server->client.
The server transmits this packet to the client to notify the client
that it has received the Accounting-Request packet and has
correctly recorded the accounting information.
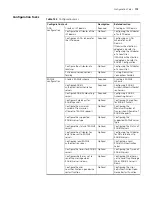
Table 132
Description on major values of the Code field (Continued)
Code
Packet type
Packet description
Table 133
RADIUS attributes
Value of the
Type field
Attribute type
Value of the
Type field
Attribute type
1
User-Name
23
Framed-IPX-Network
2
User-Password
24
State
3
CHAP-Password
25
Class
4
NAS-IP-Address
26
Vendor-Specific
5
NAS-Port
27
Session-Timeout
6
Service-Type
28
Idle-Timeout
7
Framed-Protocol
29
Termination-Action
8
Framed-IP-Address
30
Called-Station-Id
9
Framed-IP-Netmask
31
Calling-Station-Id
10
Framed-Routing
32
NAS-Identifier
11
Filter-ID
33
Proxy-State
12
Framed-MTU
34
Login-LAT-Service
Summary of Contents for 4200G 12-Port
Page 10: ...8 CONTENTS...
Page 14: ...4 ABOUT THIS GUIDE...
Page 46: ...32 CHAPTER 5 LOGGING IN THROUGH WEB BASED NETWORK MANAGEMENT SYSTEM...
Page 48: ...34 CHAPTER 6 LOGGING IN THROUGH NMS...
Page 60: ...46 CHAPTER 9 VLAN CONFIGURATION...
Page 64: ...50 CHAPTER 10 MANAGEMENT VLAN CONFIGURATION...
Page 80: ...66 CHAPTER 13 GVRP CONFIGURATION...
Page 98: ...84 CHAPTER 15 LINK AGGREGATION CONFIGURATION...
Page 112: ...98 CHAPTER 18 MAC ADDRESS TABLE MANAGEMENT...
Page 126: ...112 CHAPTER 19 LOGGING IN THROUGH TELNET...
Page 162: ...148 CHAPTER 20 MSTP CONFIGURATION...
Page 274: ...260 CHAPTER 29 IGMP SNOOPING CONFIGURATION...
Page 276: ...262 CHAPTER 30 ROUTING PORT JOIN TO MULTICAST GROUP CONFIGURATION...
Page 298: ...284 CHAPTER 33 SNMP CONFIGURATION...
Page 304: ...290 CHAPTER 34 RMON CONFIGURATION...
Page 338: ...324 CHAPTER 36 SSH TERMINAL SERVICES...
Page 356: ...342 CHAPTER 38 FTP AND TFTP CONFIGURATION...
Page 365: ...Information Center Configuration Example 351 S4200G terminal logging...
Page 366: ...352 CHAPTER 39 INFORMATION CENTER...
Page 378: ...364 CHAPTER 40 BOOTROM AND HOST SOFTWARE LOADING...
Page 384: ...370 CHAPTER 41 Basic System Configuration and Debugging...
Page 388: ...374 CHAPTER 43 NETWORK CONNECTIVITY TEST...
Page 406: ...392 CHAPTER 45 CONFIGURATION OF NEWLY ADDED CLUSTER FUNCTIONS...