196
C
HAPTER
9: D
EVICE
M
ANAGEMENT
Managing by SNMP
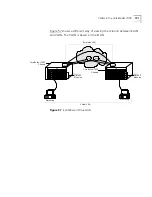
You can manage the CoreBuilder 7000 family ATM switch via
SNMP-based external network management applications running on a
workstation (see Figure 60). The 3Com Transcend
©
Enterprise Manager is
the recommended graphical user interface tool for central management
of medium to large-scale ATM networks.
Since the agent is standard-based, other SNMP-based applications, such
as SunNet Manager and HP OpenView can be used, provided that the
MIB is correctly installed at the management station.
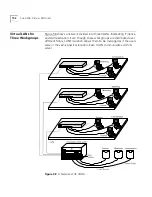
Out-of-Band Access
The CoreBuilder 7000 family ATM switch implements the SNMP agent by
out-of-band access via the Ethernet port.
Use the LMA to configure the CoreBuilder 7000 family ATM switch’s IP
address, subnet mask, NMS IP address, and the default gateway via the
LM to enable access to the SNMP agent. Refer to the Installation and
Startup Guide
for additional configuration information.
Table 45
SNMP Traps
Trap
Description
Cold start
A coldStart trap signifies that the
sending protocol entity is re-initializing
itself such that the agent’s configuration
or the protocol entity implementation
may be altered.
Link up
A linkUp trap signifies that the sending
protocol entity recognizes that one of
the communication links represented in
the agent’s configuration has come up
Link down
A linkDown trap signifies that the
sending protocol entity recognizes a
failure in one of the communication links
represented in the agent’s configuration
Module configuration change
(port-board up/down/out)
Sent whenever an IFC (interface card) is
inserted or removed from the chassis
Power supply configuration change
(up/down/out)
Sent whenever a power supply is
disconnected, inserted, or removed from
the chassis
Temperature sensor (good/bad)
Sent whenever the temperature on the
switch board exceeds a certain
hard-coded limit.
Summary of Contents for CoreBuilder 7000
Page 12: ......
Page 30: ...30 CHAPTER 1 ATM NETWORK BASICS...
Page 32: ...32 CHAPTER 1 ATM NETWORK BASICS...
Page 34: ...34 CHAPTER 1 ATM NETWORK BASICS Figure 8 LANE Network over WAN...
Page 96: ...96 CHAPTER 4 PRIVATE NETWORK TO NETWORK INTERFACE PNNI VERSION 1 0...
Page 184: ...184 CHAPTER 7 LAN EMULATION VERSIONS 1 0 AND 2 0...
Page 206: ...206 CHAPTER 9 DEVICE MANAGEMENT...
Page 222: ...222 APPENDIX A TECHNICAL SUPPORT...
Page 234: ...234 APPENDIX B PROTOCOLS AND INTERFACES...
Page 238: ...238 APPENDIX C COREBUILDER 7000 FAMILY ATM SWITCH SPECIFICATIONS...
Page 242: ...242 APPENDIX D SAFETY INFORMATION...