User Interfaces and the LANplex® 2500 System
1-3
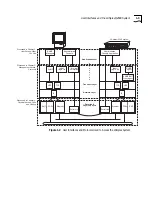
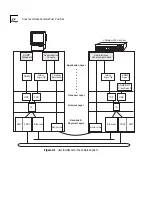
Figure 1-2
User Interfaces and Protocols Used to Access the LANplex System
Application Layer
Transport Layer
Network Layer
Data-link &
Physical Layers
SNMP
Managers
SNMP
TCP
Administration
Console Application
UDP
Ethernet
FDDI
SMT
TCP
UDP
telnet,
rlogin, ftp
SNMP/SMT
Proxy Agent
SNMP
Agent
IP
IP
Serial Line
Serial Line
Ethernet
FDDI
SMT
Administration
Console
Discussed in Chapter 2:
User Access: What
You See
Discussed in Chapter 3:
Management Access:
Protocols
Discussed in Chapter 4:
Physical Access: Ports
and Cabling
telnet,
rlogin, ftp
Terminal
Emulation
LANplex
®
2500 system
Summary of Contents for LANPLEX 2500
Page 1: ...LANPLEX 2500 OPERATION GUIDE Part No 801 00344 000 Published November 1996 Revision 03...
Page 14: ......
Page 18: ...1 4 CHAPTER 1 LANPLEX MANAGEMENT AND ADMINISTRATION OVERVIEW...
Page 78: ...III Chapter 9 FDDI Overview and Implementation Chapter 10 FDDI Networks FDDI TECHNOLOGY...
Page 97: ...IV Chapter 11 ATM Networks ATM TECHNOLOGY...
Page 116: ...V Appendix A SNMP MIB Support Appendix B Technical Support APPENDIXES...