5-8
C
HAPTER
5: T
RANSPARENT
B
RIDGING
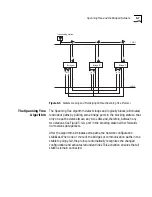
Figure 5-4
Spanning Tree Protocol Implemented to Block Redundant Links
How the Spanning Tree Algorithm Works
The Spanning Tree algorithm is based on the idea that bridges transmit
messages to each other that allow them to calculate the Spanning Tree
topology. These messages are special packets called
Configuration Bridge
Protocol Data Units
(CBPDUs), or configuration messages. CBPDUs are not
propagated through the bridge as regular data packets are. Instead, each
bridge behaves as an end-station for these packets, receiving and
interpreting them.
CBPDUs at work
The CBPDUs help the bridges establish a hierarchy among themselves (or a
calling order) for the purposes of creating a loopless network. Based on the
information in the CBPDUs, the bridges elect a
root bridge
, which is at the
top level of the hierarchy. The bridges then choose the best path on which
to transmit information to the root bridge.
The bridges chosen as the best path, called
designated bridges
, are the
second level of the hierarchy. A designated bridge “relays” the network
transmissions to the root bridge through its
root port
. Any port that
transmits to the root bridge is a root port. The designated bridges also have
designated ports
— the ports attached to the LANs from which the bridge is
Transmitting station
Bridge C
Bridge B
LAN 1
LAN 2
Bridge A
BLOCKED
BLOCKED
Summary of Contents for LANPLEX 2500
Page 1: ...LANPLEX 2500 OPERATION GUIDE Part No 801 00344 000 Published November 1996 Revision 03...
Page 14: ......
Page 18: ...1 4 CHAPTER 1 LANPLEX MANAGEMENT AND ADMINISTRATION OVERVIEW...
Page 78: ...III Chapter 9 FDDI Overview and Implementation Chapter 10 FDDI Networks FDDI TECHNOLOGY...
Page 97: ...IV Chapter 11 ATM Networks ATM TECHNOLOGY...
Page 116: ...V Appendix A SNMP MIB Support Appendix B Technical Support APPENDIXES...