8-2
C
HAPTER
8: LAN
PLEX
® B
RIDGING
E
XTENSIONS
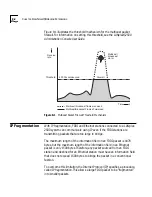
Figure 8-1 illustrates the threshold mechanism for the multicast packet
firewall. For information on setting this threshold, see the
LANplex® 2500
Administration Console User Guide
.
Figure 8-1
Multicast Packet Firewall Threshold Mechanism
IP Fragmentation
With IP fragmentation, FDDI and Ethernet stations connected to a LANplex
2500 system can communicate using IP even if the FDDI stations are
transmitting packets that are too large to bridge.
The maximum length of the information field in an FDDI packet is 4478
bytes, but the maximum length of the information field in an Ethernet
packet is only 1500 bytes. Therefore, any packet sourced from an FDDI
station and destined for an Ethernet station must have an information field
that does not exceed 1500 bytes to bridge the packet in a conventional
fashion.
To overcome this limitation, the Internet Protocol (IP) specifies a procedure,
called
IP fragmentation
. This allows a large FDDI packet to be “fragmented”
into smaller packets.
400 Packets/second
Firewall
Threshold
Time
Receive
rate
Multicast/
broadcast
storm
Multicast/broadcast frames received
Multicast/Broadcast Frames Forwarded
Summary of Contents for LANPLEX 2500
Page 1: ...LANPLEX 2500 OPERATION GUIDE Part No 801 00344 000 Published November 1996 Revision 03...
Page 14: ......
Page 18: ...1 4 CHAPTER 1 LANPLEX MANAGEMENT AND ADMINISTRATION OVERVIEW...
Page 78: ...III Chapter 9 FDDI Overview and Implementation Chapter 10 FDDI Networks FDDI TECHNOLOGY...
Page 97: ...IV Chapter 11 ATM Networks ATM TECHNOLOGY...
Page 116: ...V Appendix A SNMP MIB Support Appendix B Technical Support APPENDIXES...