37-11
ARP Attack Defense Configuration Example III
Network Requirements
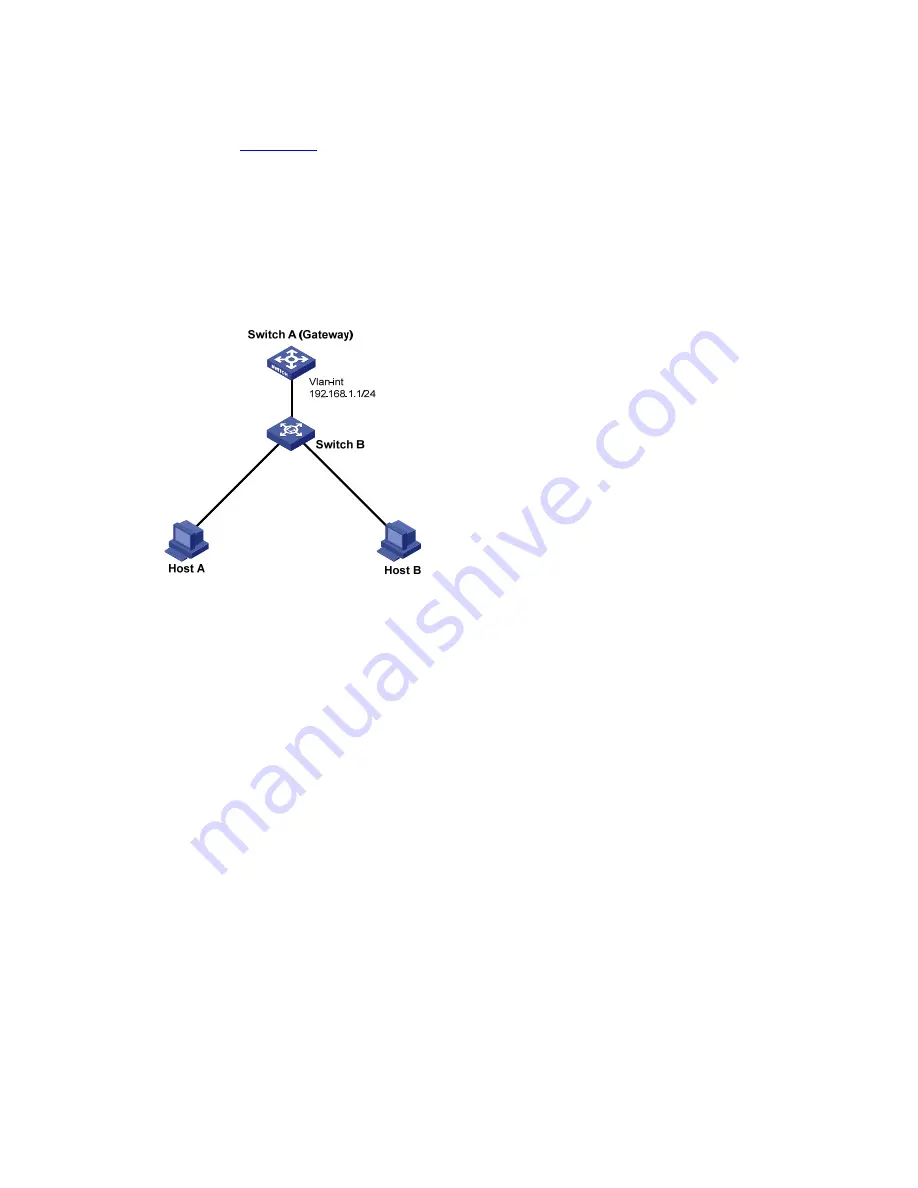
As shown in
Figure 37-5
, Host A and Host B are connected to Gateway (Switch A) through a Layer 2
switch (Switch B). To prevent ARP attacks such as ARP flooding:
z
Enable ARP packet source MAC address consistency check on Switch A to block ARP packets
with the sender MAC address different from the source MAC address in the Ethernet header.
z
Limit the number of dynamic ARP entries learned on VLAN-interface 1.
Network Diagram
Figure 37-5
Network diagram for ARP attack defense
Configuration Procedures
# Enter system view.
<SwitchA> system-view
# Enable ARP source MAC address consistency check.
[SwitchA] arp anti-attack valid-check enable
# Enter VLAN-interface 1 view.
[SwitchA] interface vlan-interface 1
# Configure an IP address for VLAN-interface 1.
[SwitchA-Vlan-interface1] ip address 192.168.1.1 24
# Configure the maximum number of ARP entries that can be learned by VLAN-interface 1 as 500.
[SwitchA-Vlan-interface1] arp max-learning-num 500
[SwitchA-Vlan-interface1] quit
ARP Attack Defense Configuration Example IV
Network Requirements
z
Host A is assigned with an IP address statically and installed with an 802.1x client.
z
A CAMS authentication, authorization and accounting server serves as the authentication server.
















































