All these new applications have one thing in common, that is, they have special requirements for
bandwidth, delay, and jitter. For instance, bandwidth, delay, and jitter are critical for videoconference
their destinations, better network services are demanded, such as
allocating dedicated bandwidth, reducing packet loss ratio, avoiding congestion, regulating network
ets. To meet those requirements, the network should be provided
and VoD. As for other applications, such as transaction processing and Telnet, although bandwidth is
not as critical, a too long delay may cause unexpected results. That is, they need to get serviced in time
even if congestion occurs.
Newly emerging applications demand higher service performance from IP networks. In addition to
simply delivering packets to
traffic, and setting priority of the pack
with better service capability.
Major Traffic Control Techniques
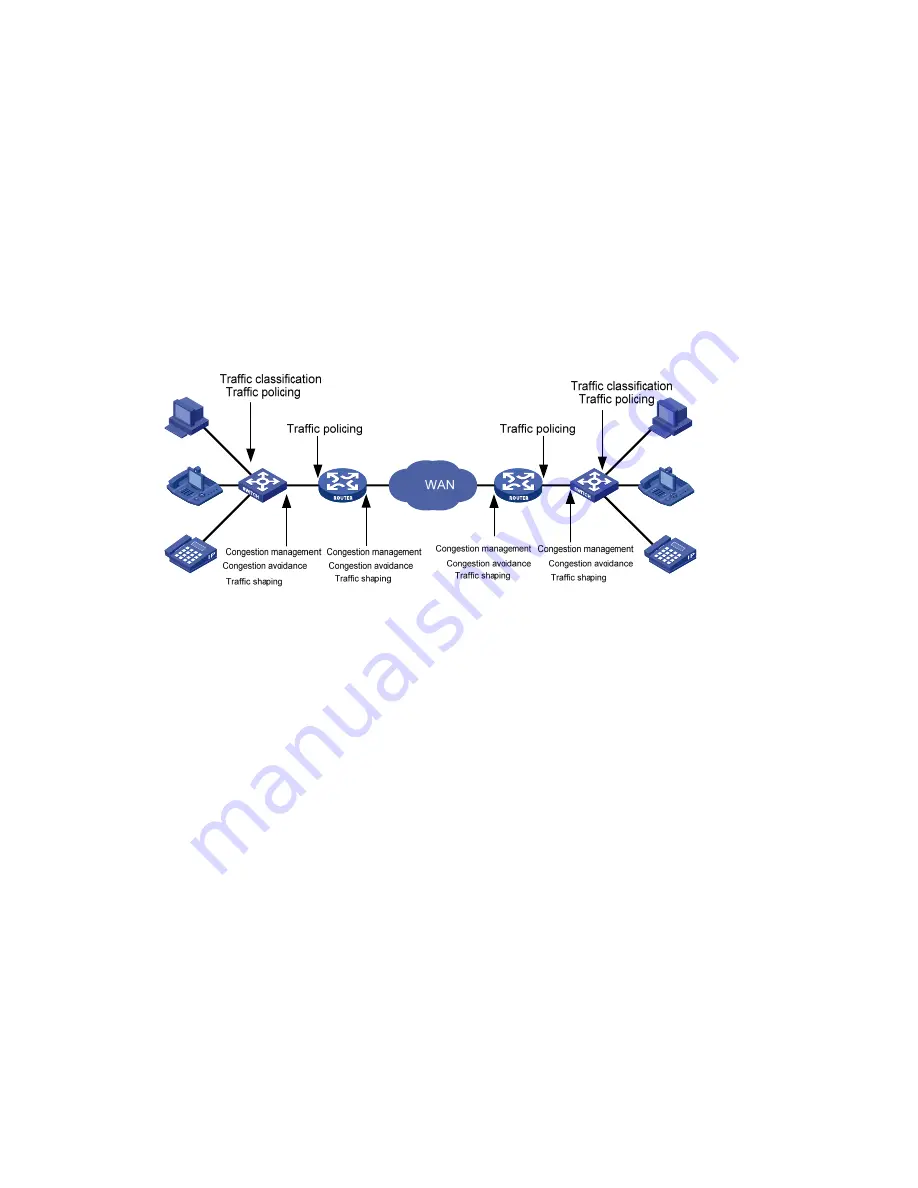
Figure 45-1
End-to-end QoS model
As shown in the figure above, traffic classification, traffic policing, traffic shaping, congestion
agement, and congestion avoidance are the foundations for a network to prov
man
ide differentiated
v
z
inbound direction of a port.
arrier benefits and network resources.
tion of a port.
It
d services possible. Traffic policing, traffic
dance are methods for implementing network
traffic control and network resource management. They are occurrences of differentiated services.
ser ices. They are described as follow:
Traffic classification identifies traffic based on certain matching rules. It is a prerequisite for
differentiated services and is usually applied in the
z
Traffic policing confines traffic to a specific specification and is usually applied in the inbound
direction of a port. You can configure restriction or penalty measures against the exceeding traffic
to protect c
z
Traffic shaping adapts output traffic rate usually to the input capability of the receiving device to
avoid packet drop and port congestion. Traffic shaping is usually applied in the outbound direction
of a port.
z
Congestion management handles resource competition during network congestion. Generally, it
adds packets to queues first, and then forwards the packets by using a scheduling algorithm.
Congestion management is usually applied in the outbound direc
z
Congestion avoidance monitors the use of network resources and drops packets actively when
congestion reaches certain degree. It relieves network load by adjusting traffics. Congestion
avoidance is usually applied in the outbound direction of a port.
Traffic classification is the basis of all the above-mentioned traffic management technologies.
identifies packets using certain rules and makes differentiate
shaping, congestion management, and congestion avoi
45-2
















































