3e-525A Outdoor Access Point
26
29000132-001 A
29000132-001 A
27
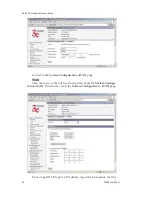
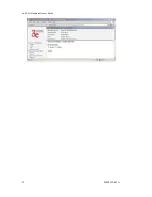
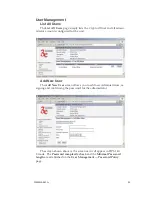
WEP encryption provides some measure of security.
Utilities exist for scanning for networks and logging all the networks
it runs into—including the real SSIDs, the access point’s MAC address,
the best signal-to-noise ratio encountered, and the time the user crossed
into the network’s space. These utilities can be used to determine whether
your network is unsecured. Note that, if WEP is enabled, that same WEP
key must also be set on each wireless device that is to become part of the
wireless network, and, if "shared key" is accepted, then each wireless de-
vice must also be coded for "shared key". To use WEP encryption, iden-
tify the level of encryption, the Default WEP key and designate the WEP
keys as shown on the screen.
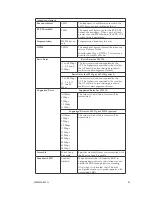
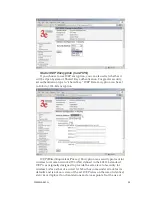
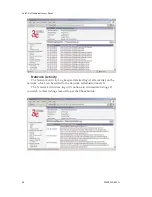
WPA (non-FIPS)
Wi-Fi Protected Access or WPA was designed to enable use of wire-
less legacy systems employing WEP while improving security. WPA uses
improved data encryption through the temporal key integrity protocol
(TKIP) which scrambles keys using a hashing algorithm and, by adding
an integrity-checking feature, ensures that the keys haven’t been tam-
pered with. In addition, user authentication is enabled using the exten-
sible authentication protocol (EAP).
WPA is an interim standard that will be replaced with the IEEE’s
802.11i standard upon its completion. However, it is expected to remain
Summary of Contents for 3e-525A
Page 3: ...This page intentionally left blank ...
Page 9: ...vi 29000132 0001 A This page intentionally left blank ...
Page 41: ...3e 525A Outdoor Access Point 32 29000132 001 A ...
Page 53: ...3e 525A Outdoor Access Point 44 29000132 001 A This page intentionality left blank ...
Page 105: ...3e 525A Wireless Access Point 96 29000132 001 A This page intentionally left blank ...