3e–527A3 Wireless Access Point – 8 Port
Chapter 3: Access Point Configuration
24
29000152-001 B
3e–527A3 Wireless Access Point – 8 Port
Chapter 3: Access Point Configuration
29000152-001 B
25
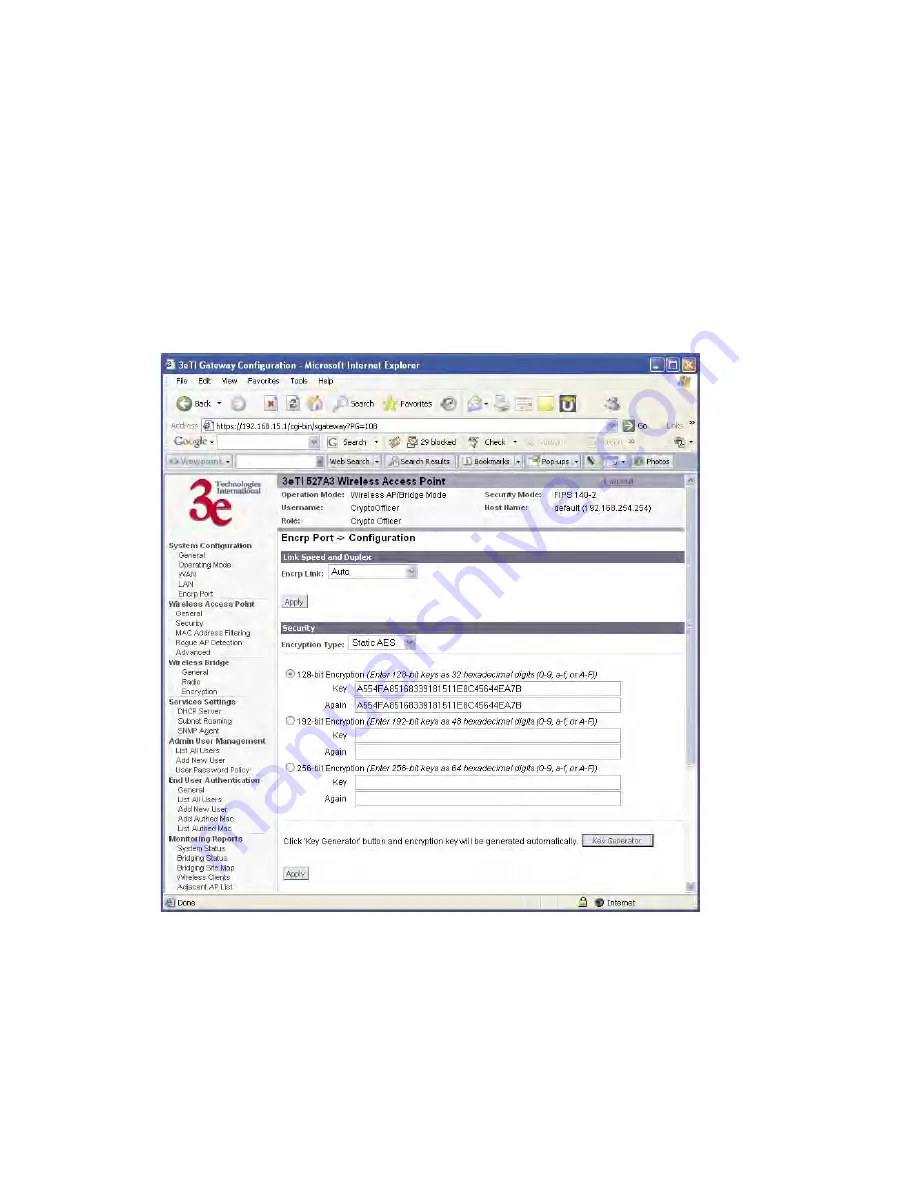
Static AES Key
The Advanced Encryption Standard (AES) uses a 128-bit block cipher
algorithm and encryption technique for protecting computerized infor-
mation. With the ability to use even larger 192-bit and 256-bit keys, if
desired, it offers higher security against brute-force attacks than the older
56-bit DES keys.
The Key Generator button automatically generates a randomized key
of the appropriate length. This key is initially shown in plain text so the
user has the opportunity to copy the key. Once the key is applied, the key
is no longer displayed in plain text.