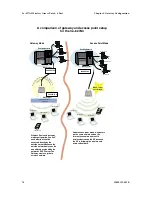
3e–527A3 Wireless Access Point – 8 Port
Chapter 3: Access Point Configuration
56
29000152-001 B
3e–527A3 Wireless Access Point – 8 Port
Chapter 3: Access Point Configuration
29000152-001 B
57
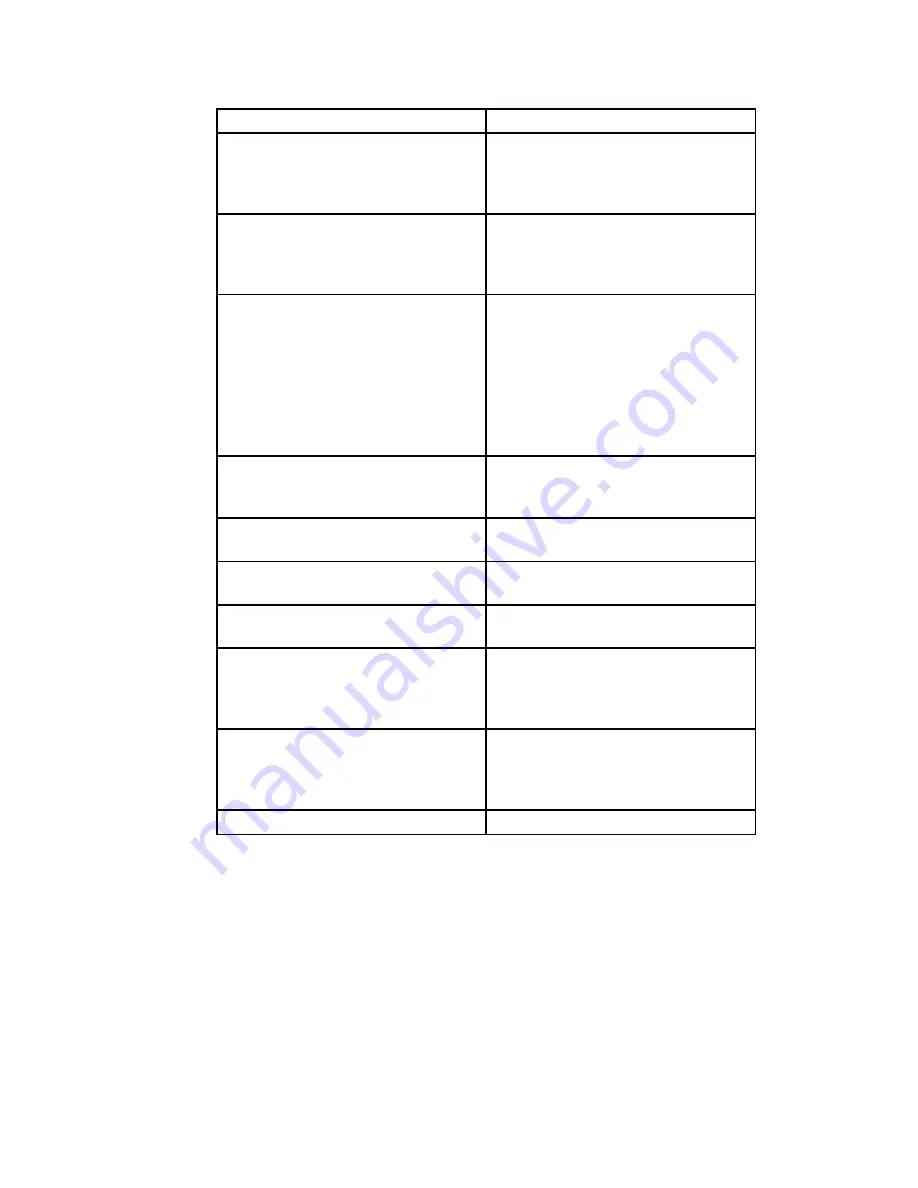
Event Type
Description
Audit Log Configuration Modified Any modification to the audit log
configuration (enable/disable,
recorded event types, etc) will trig-
ger the creation of an audit record.
Key Transfer Error
Any error detected during the
dynamic key exchange, either to
the station or the authentication
server.
Key Zeroized
The keys are zeroized including:
1. Transitioning from static key to
DKE (and vice versa)
2. Transitioning to bypass mode
Individual log messages appear
from the application and driver
since keys are held in both loca-
tions.
STA Failed Authentication
A station's authentication request
is dropped because it doesn't
match the MAC address filter.
STA Associated
A station successfully associates to
the AP.
Encryption Algorithm Changed
The encryption algorithm is
changed, including bypass mode.
Failed FIPS Policy
All HMAC/AES decrypt errors
that can be detected.
MAC Filter Changed
The MAC address filter is changed
including adding/deleting,
enable/disable, and changing filter
type.
Time Changed
Whenever the time is changed via
the GUI or at bootup if the time is
within two minutes of 11/30/1999,
0hr, 0min.
Self Test Activated
The self-test function is run.