3e–525C–3 Wireless Access Point
Chapter 3: Access Point Configuration
34
29000171-001 A
3e–525C–3 Wireless Access Point
Chapter 3: Access Point Configuration
29000171-001 A
35
IEEE 802.11i and WPA
Wi-Fi Protected Access or WPA was designed to enable use of wire-
less legacy systems employing WEP while improving security. WPA uses
improved data encryption through the temporal key integrity protocol
(TKIP) which scrambles keys using a hashing algorithm and, by adding
an integrity-checking feature, ensures that the keys haven’t been tam-
pered with. In addition, user authentication is enabled using the exten-
sible authentication protocol (EAP).
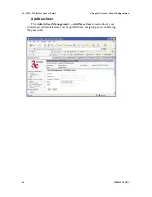
If you wish to use WPA on the 3e–525C–3, enable either WPA Pre-
shared Key Settings or WPA 802.1x Settings.
If you are a SOHO user, selecting pre-shared key means that you
don’t have the expense of installing a Radius Server. Simply input up to
63 character / numeric / hexadecimals in the Passphrase field. If your
clients use WPA-TKIP, select TKIP as encryption type. If your clients use
WPA-AES, select AES-CCMP. If a combination, select AUTO.
Enable pre-authentication to allow a client to authenticate in advance
with the AP before the client is associated with it. Allowing the AP to
pre-authenticate a client decreases the transition time when a client roams
between APs.
As an alternative, for business applications who have installed Radius
Servers, select WPA 802.1x and input the Primary Radius Server settings.
Use of Radius Server for key management and authentication requires
that you have installed a separate certification system and each client
must have been issued an authentication certificate.
Re-keying time is the frequency in which new encryption keys are
generated and distributed to the client. The more frequent re-keying, the
better the security. For highest security, select the lowest re-keying inter-
val.
Once you have selected the options you will use, click
Apply
.