3e–525C–3 Wireless Access Point
Chapter 3: Access Point Configuration
52
29000171-001 A
3e–525C–3 Wireless Access Point
Chapter 3: Access Point Configuration
29000171-001 A
53
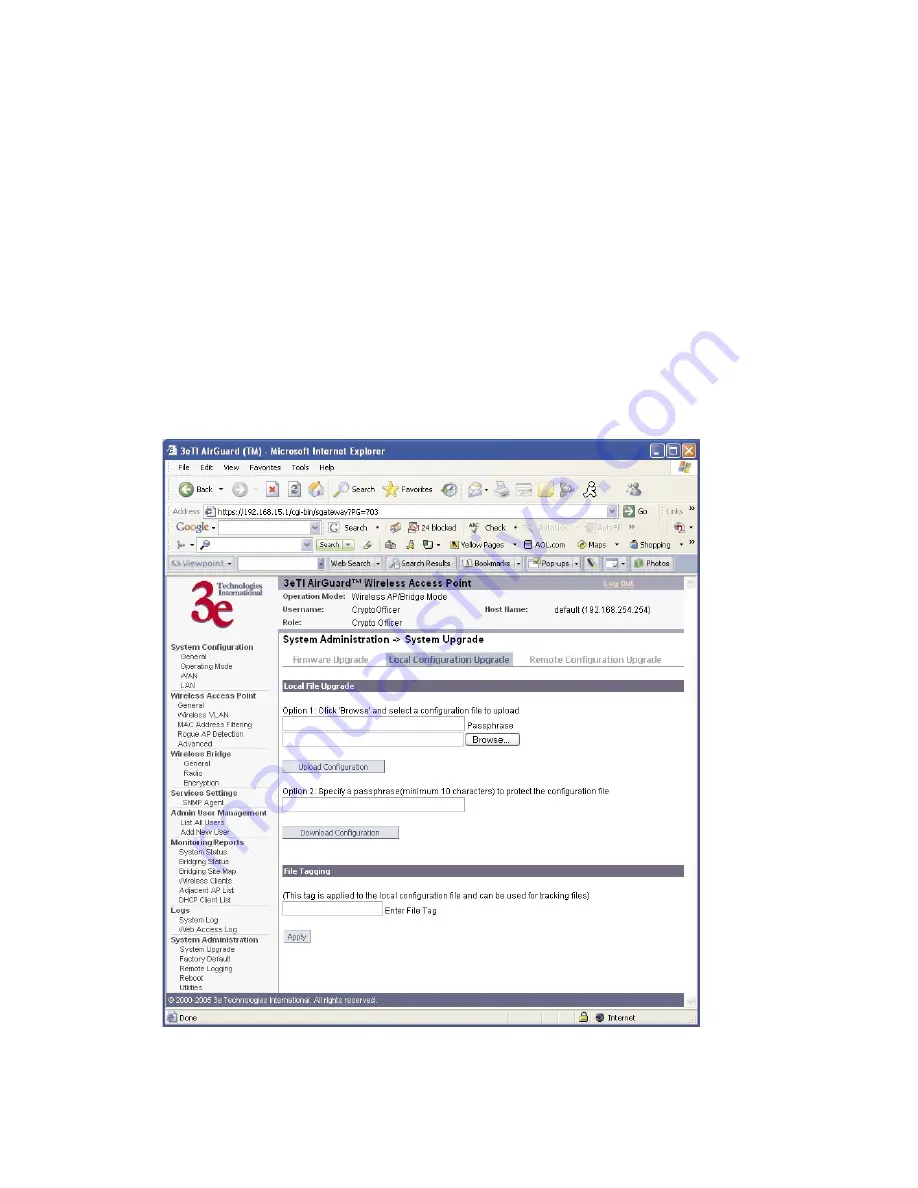
Local Configuration Upgrade
On the
System Administration — System Upgrade
screen, click on
the
Local Configuration Upgrade
tab to upload and download configura-
tion files to access points connected to the network.
To upload a configuration file, select the file using the browse but-
ton and enter the passphrase for that file. The passphrase protects the file
from unauthorized users. It prevents unauthorized users from applying
the system configuration file to an unauthorized AP to gain access to the
network. Before downloading the system configuration file to a local com-
puter, the user must enter a passphrase to protect the file. Before the sys-
tem configuration file can be uploaded onto another AP, the passphrase
must be entered on the remote AP.
The configuration file can be tagged with a 12 character tag to keep
track of the configuration file as it is transferred to other APs.