User manual
16
If priority queue bandwidth configuration is available, must mark the enter into port‘s data pack as CoS.
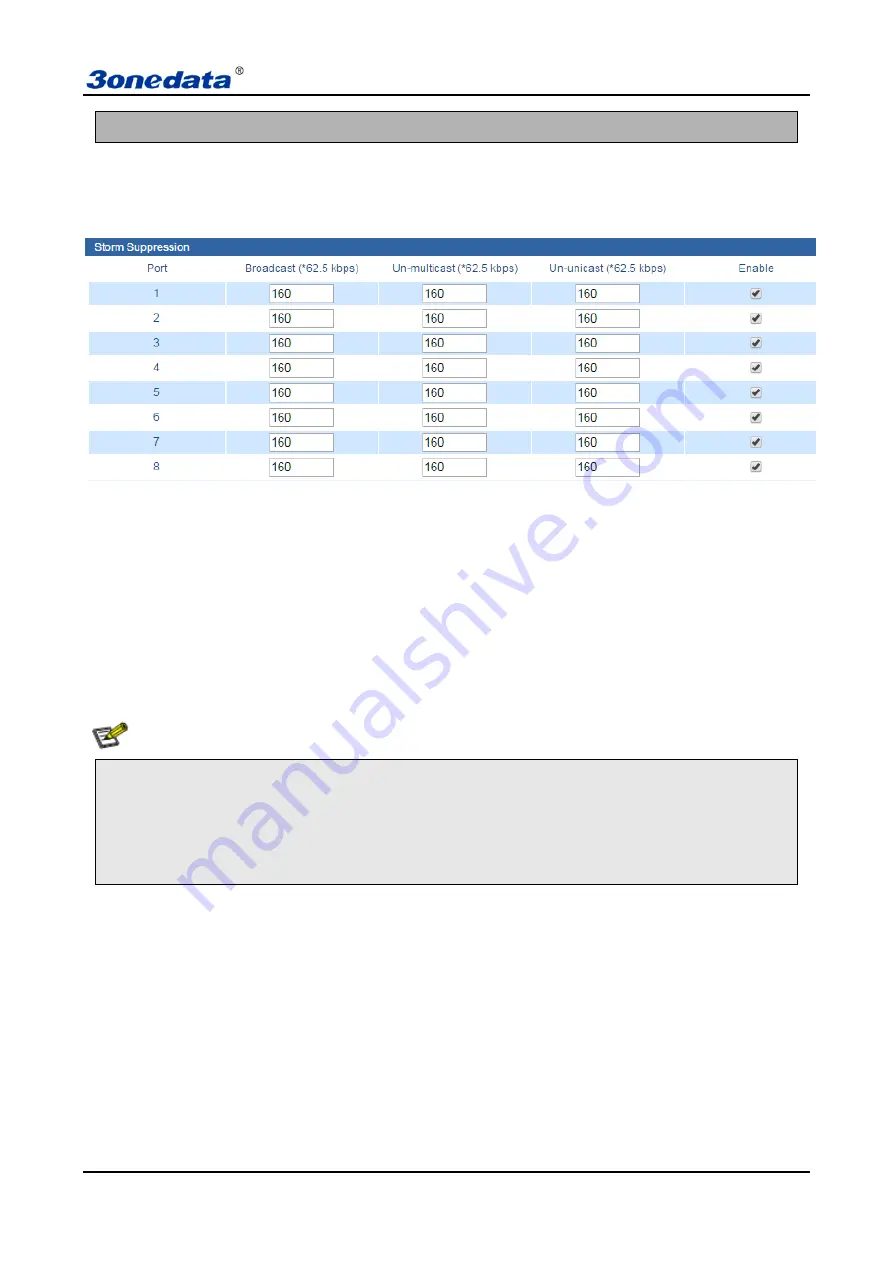
5.5.3 Storm Suppression
Broadcast storm is the accumulation of broadcast and multicast traffic on a computer network. Extreme amounts
of broadcast traffic constitute a broadcast storm. A broadcast storm can consume sufficient network resources so
as to render the network unable to transport normal traffic.
(
Figure5.5.5
)
There are many reasons to cause broadcast storm. For example: a redundant or incorrect connect among switches.
If enable storm suppression, it can stop the attack. Our device can detect 3 kinds of broadcast messages according
to the type of broadcast storm.
Broadcast packets: data frame of the destination address of FF-FF-FF-FF-FF-FF
Multicast packets: destination address is XX-XX-XX-XX-XX-XX data frames, second x is odd numbers
such as 1, 3, 5, 7, 9, b, d, and f, x represents any digit.
Unicast: unicast is the term used to describe communication where a piece of information is sent from one
point to another point. In this case there is just one sender, and one receiver.
Destination lookup failure frame: the MAC address of this data frame doesn't exist in inside index. It needs
to transmit to all the ports, including unicast and multicast flow.
1.
The maximum length of Ethernet data frames is 1518 bytes, and each 64Kb of data communication includes about 6
Ethernet data frames with 1518-byte.
2.
The minimum length of Ethernet data frames is 64 bytes. Each 64 Kb of data communication includes about 128 Ethernet
data frames with 64-byte.
3.
In the network the broadcast packets are more than 800packet/s, the network delay is obvious.
4.
The recommended setting is 3% based on the above theory.
5.
Please be caution to use MAC control frame and destination lookup failure frame, disabling IGMP Snooping will have
impact on the transmission of the multicast.
5.6 L2 Features
5.6.1 Based on port VLAN
Port VLAN provides a solution that can divide the ports of switch into different virtual private domain. The data
cannot be exchanged in the different private domain, so it's more secure to maintenance.
About port VLAN
,
different VLAN with different identity. Use the same ID identity will lead to internal
members of the group be replaced, the new ID identity will create a new forwarding rule; all ports must belong to
one or more VLAN.