64
User Manual ENGLISH
WHG-Series Wireless WLAN Controller
Copyright © 2017, 4ipnet, Inc. All rights reserved. All other trademarks mentioned are the property of their respective owners.
5
How to configure User Policies
User Policy, as the term suggests, are profiles of network governing constraints which are enforced upon
users, including firewall rules, login schedule, routing rules and session allowances. There is a Global policy,
which will be applied if a user belongs to a Group not bound to any Policy. The number of Policy profiles
will be model dependent.
1.1
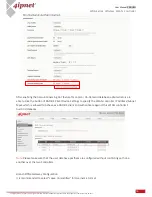
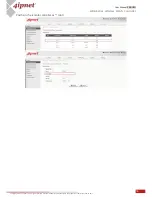
User Policy
Select Policy: to choose which User Policy profile to configure.
Firewall Profile: to specify the protocols & rules that will be enforced to users governed by User Policy
-
Service Protocol: This link leads to a policy's Service List page where the administrator can
defined a list of services by protocols (TCP/UDP/ICMP/IP). The service names defined here forms
a choice list for configuring firewall rules.
-
User Firewall Rules: This link leads to the policy's Firewall Rules page. Rule No. 1 has the highest
priority; rule No. 2 has the second priority, and so on. Each firewall rule is defined by Source,
Destination, a Service out of the policy's Service List and a Pass/Block action. Optionally, a
Firewall Rule Schedule can be set to specify when the firewall rule is enforced; it can be set to
Always, Recurring or One Time.
Privilege Profile: to configure the flexibility and privilege for each user.