Functions
State Dependencies
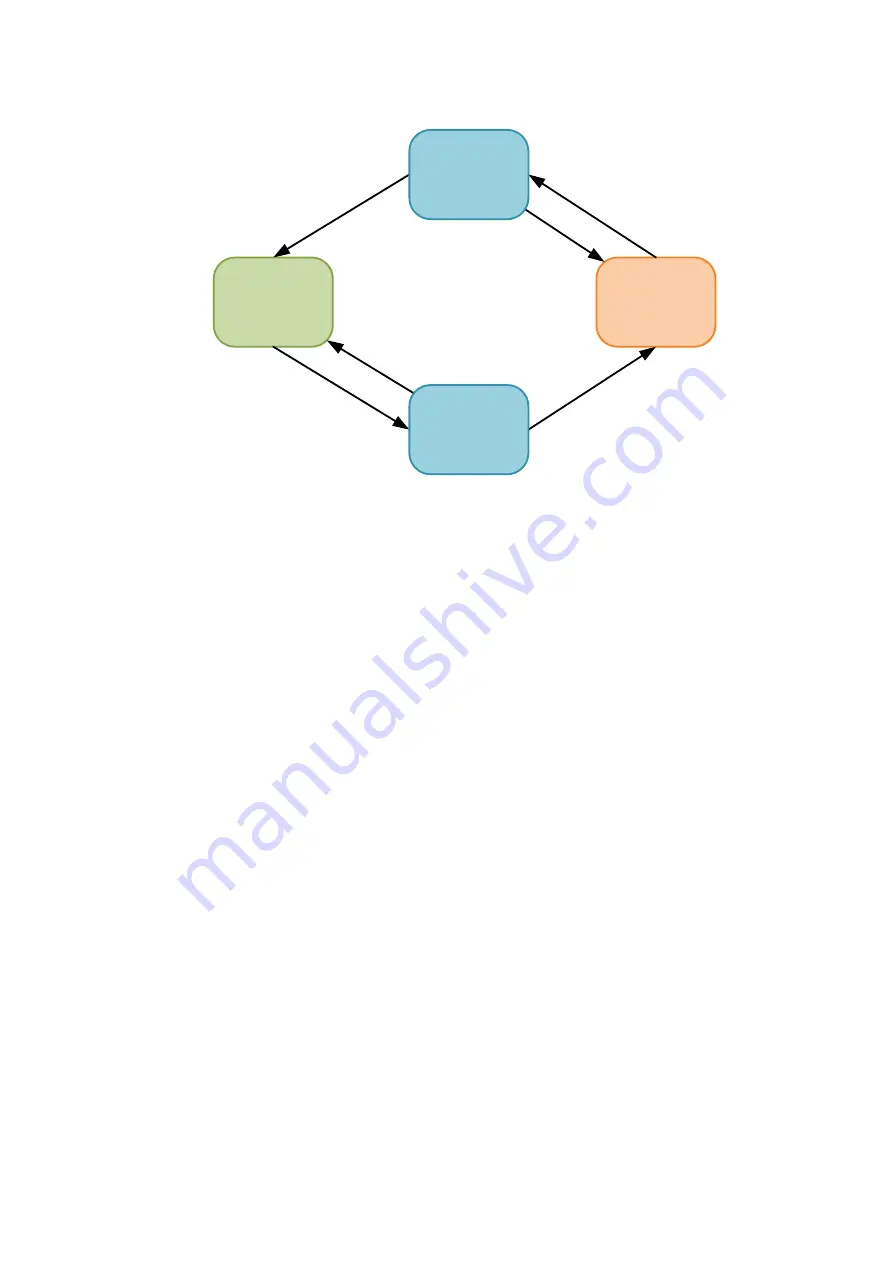
Monitor:
Monitor:
Monitor condition
Monitor condition
Monitor condition
Monitor condition
Monitor switching
Monitor
Monitor:
Monitor:
entered
lost
lost
normal state
(up)
delay over
(hold down)
delay state
entered
(down)
backup state
switching delay over
(hold up)
delay state
Figure 29: State transitions of the monitor
Commands for the monitor:
< s e t m o n i t o r e n a b l e >
< s e t m o n i t o r n o e n a b l e >
< s e t m o n i t o r t a r g e t - i p { I P a d d r e s s } >
< s e t m o n i t o r i n t e r v a l { 1 0 0 - 6 0 0 0 0 } >
< s e t m o n i t o r s w i t c h i n g - d e l a y { 1 - 3 0 0 } >
< s e t m o n i t o r a l a r m - i f - d o w n >
< s e t m o n i t o r n o a l a r m - i f - d o w n >
< s e t m o n i t o r a l a r m - i f - u p >
< s e t m o n i t o r n o a l a r m - i f - u p >
2.30 State Dependencies
EDS500 devices offer the option to bind certain settings to certain conditions, e.g. the
link state of another interface (Link Fault Pass-Through, LFPT) or to a monitor (refer to
Chapter 2.29, "Monitor"). Further settings for dependencies deal with the selection of the
source VLAN for system services and serial tunnelling.
Commands to configure state dependencies
< s e t s w i t c h { p o r t 1 | p o r t 2 | p o r t 3 | p o r t 4 } d e p e n d e n c y
{ c h a n n e l 0 | d s l 1 | d s l 2 | i n v e r s e - m o n i t o r | m o n i t o r | n o n e } >
{ i n v e r s e m o n i t o r | m o n i t o r | n o n e } >
< s e t i n t e r f a c e c o n s o l e s o u r c e v l a n { 1 - 4 0 9 4 } [ d e p e n d e n c y
{ i n v e r s e - m o n i t o r | m o n i t o r } ] >
< c l e a r i n t e r f a c e c o n s o l e s o u r c e v l a n [ { 1 - 4 0 9 4 } ] >
< s e t s y s t e m r a d i u s s o u r c e v l a n { 1 - 4 0 9 4 } [ d e p e n d e n c y
{ i n v e r s e - m o n i t o r | m o n i t o r } ] >
< c l e a r s y s t e m r a d i u s s o u r c e v l a n [ { 1 - 4 0 9 4 } ] >
< s e t s y s t e m s n m p t r a p - s o u r c e v l a n { 1 - 4 0 9 4 } [ d e p e n d e n c y
1KGT151021
V000 1
103