4.
Web Management
AirLive AirMax4GW User’s Manual
42
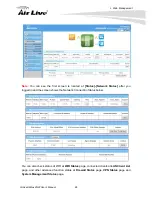
By default, all the LAN ports and virtual APs belong to one VLAN group, and
this VLAN ID is forced to “1” but noted as "None" for avoiding misunderstanding.
It is a special Tag-based VLAN group for the Intranet of device to operated, there
is no tag required in Intranet packets for this default VLAN group with that ID.
Also be noted, there is only one Ethernet LAN port in the device.
If you want to configure your own tag-based VLANs, click on the “Edit” button on
a new VLAN ID row.
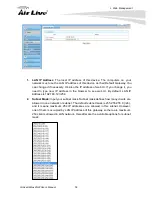
1. VLAN ID
: Specify a VLAN tag for this VLAN group. The ports with the same VID are
in the same VLAN group.
2. Internet
: Specify whether this VLAN group can access Internet or not. If it is
checked, all the packet will be un-tagged before it is forward to Internet, and all the
packets from Internet will be tagged with the VLAN ID before it is forward to the
destination belongs to this configuring VLAN group in the Intranet.
3. Port-1, VAP-1 ~ VAP-8
: Specify whether they belong to the VLAN group or not. You
just have to check the boxes for dedicated ports.
4. DHCP Server
: Specify a DHCP server for the configuring VLAN group. This
device provides only one DHCP server to serve the DHCP requests from different
VLANs.
Afterwards, click on “Save” to store your settings or click “Undo” to give up
the changes.