20. Web VPN / SSL VPN
179
AirLive RS-2500 User’s Manual
STEP 5
﹒
Configure the setting from a browser
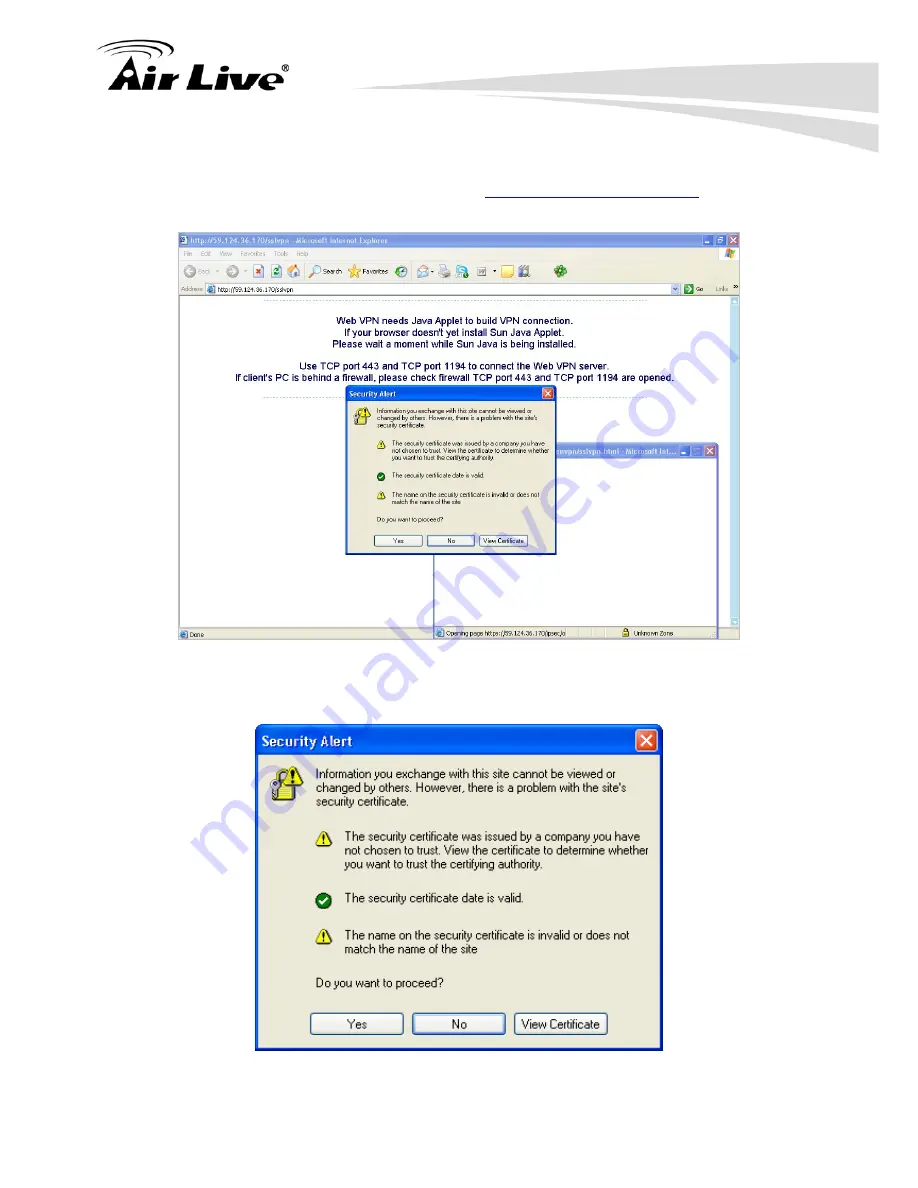
Enter http://61.11.11.11/sslvpn or
http://59.124.36.170/webvpn
:
in the
URL
field (the RS-2500 interface address plus sslvpn or webvpn). (Figure 20-10)
Figure 20-10 Login SSL VPN Screen
Click
Yes
in the Security Alert window. (Figure 20-11)
Figure 20-11 Security Alert Window
Summary of Contents for RS-2500
Page 1: ...User s Manual Dual WAN Security VPN Gateway RS 2500 ...
Page 218: ...22 Monitor 213 AirLive RS 2500 User s Manual Figure 22 23 To Detect WAN Statistics ...
Page 220: ...22 Monitor 215 AirLive RS 2500 User s Manual Figure 22 25 To Detect Policy Statistics ...
Page 224: ...22 Monitor 219 AirLive RS 2500 User s Manual Figure 22 30 Traceroute Results ...
















































