C
C
C
h
h
h
a
a
a
p
p
p
t
t
t
e
e
e
r
r
r
1
1
1
5
5
5
P
P
P
o
o
o
l
l
l
i
i
i
c
c
c
y
y
y
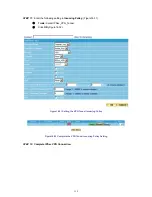
Every packet has to be detected if it corresponds with Policy or not when it passes the RS-3000. When
the conditions correspond with certain policy, it will pass the RS-3000 by the setting of Policy without
being detected by other policy. But if the packet cannot correspond with any Policy, the packet will be
intercepted.
The parameter of the policy includes Source Address, Destination Address, Service, Schedule,
Authentication User, Tunnel, Action-WAN Port, Traffic Log, Statistics, Content Blocking, IM/P2P
Blocking, QoS, MAX. Bandwidth Per Source IP, MAX. Concurrent Sessions Per IP and MAX.
Concurrent Sessions. Control policies decide whether packets from different network objects, network
services, and applications are able to pass through the RS-3000.
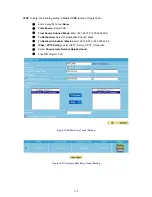
How to use Policy?
The device uses policies to filter packets. The policy settings are: source address, destination address,
services, permission, packet log, packet statistics, and flow control. Based on its source addresses, a
packet can be categorized into:
(1)
Outgoing:
The source IP is in LAN network; the destination is in WAN network. The system
manager can set all the policy rules of Outgoing packets in this function
(2)
Incoming:
The source IP is in WAN network; the destination is in LAN network. (For example:
Mapped IP, Virtual Server) The system manager can set all the policy rules of Incoming
packets in this function
(3)
WAN to DMZ:
The source IP is in WAN network; the destination is in DMZ network. (For
example: Mapped IP, Virtual Server) The system manager can set all the policy rules of WAN
to DMZ packets in this function
(4)
LAN to DMZ:
The source IP is in LAN network; the destination is in DMZ network. The system
manager can set all the policy rules of LAN to DMZ packets in this function
(5)
DMZ to LAN:
The source IP is in DMZ network; the destination is in LAN network. The system
manager can set all the policy rules of DMZ to LAN packets in this function
(6)
DMZ to WAN:
The source IP is in DMZ network; the destination is in WAN network. The
system manager can set all the policy rules of DMZ to WAN packets in this function
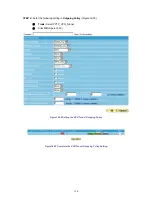
All the packets that go through RS-3000 must pass the policy permission. Therefore, the LAN,
WAN, and DMZ network have to set the applicable policy when establish network connection.
126
Summary of Contents for RS-3000
Page 1: ...1 RS 3000 Office UTM Gateway User s Manual ...
Page 45: ...Figure 5 11 PPTP Connection Figure 5 12 Complete PPTP Connection Setting 43 ...
Page 133: ...Figure15 3 Traffic Log Monitor WebUI 131 ...
Page 142: ...Figure15 19 Complete Policy Setting 140 ...
Page 183: ...Figure17 33 Create Folder WebUI 181 ...
Page 185: ...Figure17 35 Select Folder for Spam Mail to move to 183 ...
Page 187: ...Figure17 37 Compact SpamMail Folder 185 ...
Page 189: ...Figure17 39 Copy the File Address that SpamMail File Store 187 ...
Page 192: ...Figure17 42 Confirm that All of the Mail in SpamMail File had been Deleted 190 ...
Page 194: ...Figure17 44 Create Folder Function WebUI 192 ...
Page 196: ...Figure17 46 Select the Folder for Needed Spam Mail to Move to 194 ...
Page 198: ...Figure17 48 Compact HamMail File 196 ...
Page 200: ...Figure17 50 Copy the File Address that HamMail File Store 198 ...