C
C
C
h
h
h
a
a
a
p
p
p
t
t
t
e
e
e
r
r
r
1
1
1
2
2
2
A
A
A
p
p
p
p
p
p
l
l
l
i
i
i
c
c
c
a
a
a
t
t
t
i
i
i
o
o
o
n
n
n
B
B
B
l
l
l
o
o
o
c
c
c
k
k
k
i
i
i
n
n
n
g
g
g
RS-3000 Application Blocking offers the system to block the connection of applications, such as
IM
,
P2P
,
Video/Audio Application
,
Webmail
,
Game Application
,
Tunnel Application
, and
Remote
Control Application
.
【
Application Signature Definition
】
:
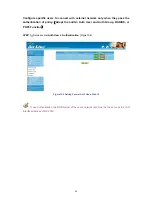
System will automatically check new signature per every
one hour, or user can also click “
Update NOW
” button to check new signature. (Figure 12-1)
Figure 12-1 Application Signature Definition WebUI
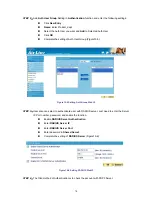
【
Instant Message Login
】
:
Restrict the authority to login MSN, Yahoo Messenger, ICQ/AIM,
QQ/TM2008, Skype, Google Talk, Gadu-Gadu, Rediff, WebIM, and AllSoft. (Figure 12-2)
Figure 12-2 Instant Message Login WebUI
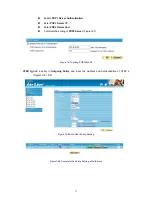
【
Instant Message File Transfer
】
:
Restrict the authority to transfer file from MSN, Yahoo
Messenger, ICQ/AIM, QQ, Skype, Google Talk, and Gadu-Gadu. (Figure 12-3)
Figure 12-3 Instant Message File Transfer WebUI
Due to the hardware limitation, it is not possible to block all kinds of application in the world, so
we just choose to block some popular application. If you require RS-3000 to block a specific application
please contact with AirLive Support Team. We will evaluate the application and try to improve it.
83
Summary of Contents for RS-3000
Page 1: ...1 RS 3000 Office UTM Gateway User s Manual ...
Page 45: ...Figure 5 11 PPTP Connection Figure 5 12 Complete PPTP Connection Setting 43 ...
Page 133: ...Figure15 3 Traffic Log Monitor WebUI 131 ...
Page 142: ...Figure15 19 Complete Policy Setting 140 ...
Page 183: ...Figure17 33 Create Folder WebUI 181 ...
Page 185: ...Figure17 35 Select Folder for Spam Mail to move to 183 ...
Page 187: ...Figure17 37 Compact SpamMail Folder 185 ...
Page 189: ...Figure17 39 Copy the File Address that SpamMail File Store 187 ...
Page 192: ...Figure17 42 Confirm that All of the Mail in SpamMail File had been Deleted 190 ...
Page 194: ...Figure17 44 Create Folder Function WebUI 192 ...
Page 196: ...Figure17 46 Select the Folder for Needed Spam Mail to Move to 194 ...
Page 198: ...Figure17 48 Compact HamMail File 196 ...
Page 200: ...Figure17 50 Copy the File Address that HamMail File Store 198 ...