encrypted channel. Unlike EAP-TLS, EAP-TTLS requires only server-side
certificates.
iv.
LEAP: Light Extensible Authentication Protocol. It is an EAP authentication type
used primarily in Cisco Aironet WLANs. It encrypts data transmissions using
dynamically generated WEP keys, and supports mutual authentication.
v.
MD5-Challenge: Message Digest Challenge. Challenge is an EAP authentication
type that provides base-level EAP support. It provides for only one-way
authentication - there is no mutual authentication of wireless client and the network.
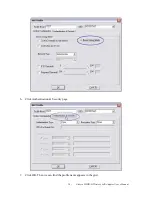
2.
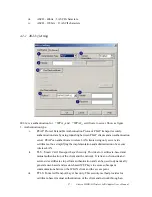
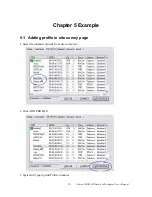
Session Resumption: user can choose “ Disable ”, “ Reauthentication ”, “ Roaming ”,
“ SameSsid ” and “ Always ”.
3.
Identity and Password: Identity and password for server.
4.
Use Client Certicate: Client Certicate for server authentication.
5.
Tunnel Authentication
i.
Protocol: Tunnel protocol, List information include “ EAP-MSCHAP ”,
“ EAP-MSCHAP v2 ”, “ CAHAP ” and “ MD5 ”
ii.
Tunnel Identity: Identity for tunnel.
iii.
Tunnel Password: Password for tunnel.
6.
CA Server: Certificate Authority Server. Each certificate is signed or issued by it. The detail
operation will explain in section 4-2-2 CA Server
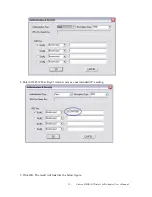
4-2-2
CA Server
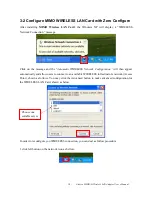
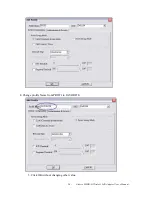
Depending on the EAP in use, only the server or both the server and client may be authenticated and
require a certificate. Server certificates identify a server, usually an authentication or RADIUS
server to clients. Most EAPs require a certificate issued by a root authority or a trusted commercial
CA. Show as the figure.
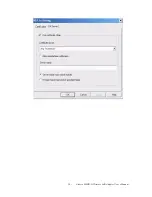
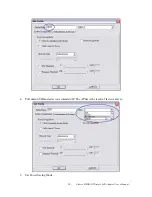
1.
Certificate issuer: Choose use server that issuer of certificates.
2.
Allow intimidate certificates: It must be in the server certificate chain between the server
certificate and the server specified in the certificate issuer must be field.
3.
Server name: Enter an authentication sever root.
- 18 -
AirLive MIMO-G Wireless LAN Adapter User’s Manual