StorTrends® 1300 User’s Guide (StorTrends iTX version 2.7)
258
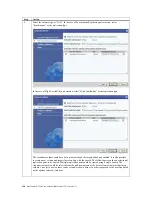
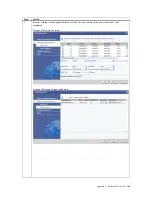
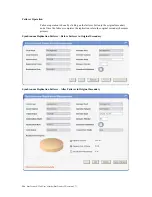
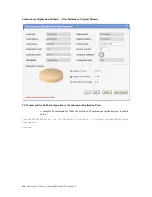
Synchronous Replication Failback – After Failback in Original Primary
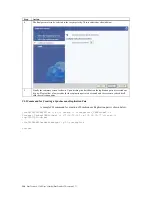
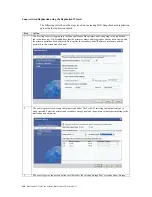
CLI Command for Failback Operations of Synchronous Replication Pairs
A sample CLI command for failback operation of Synchronous replication pair is shown
below:
[root@ITX0030488657ee ~]# cli perform -t failback -l Storage1_SecReplSANVolume1
syncreplica
Success.
Summary of Contents for ManageTrends 2.7
Page 18: ...StorTrends 1300 User s Guide StorTrends iTX version 2 7 xviii...
Page 24: ...StorTrends 1300 User s Guide StorTrends iTX version 2 7 6...
Page 33: ...Chapter Two Chassis Set Up 15 Accessing the Inside of the System...
Page 60: ...StorTrends 1300 User s Guide StorTrends iTX version 2 7 42...
Page 64: ...StorTrends 1300 User s Guide StorTrends iTX version 2 7 46...
Page 70: ...StorTrends 1300 User s Guide StorTrends iTX version 2 7 52...
Page 100: ...StorTrends 1300 User s Guide StorTrends iTX version 2 7 82...
Page 106: ...StorTrends 1300 User s Guide StorTrends iTX version 2 7 88 Control Panel...
Page 236: ...StorTrends 1300 User s Guide StorTrends iTX version 2 7 218...
Page 256: ...StorTrends 1300 User s Guide StorTrends iTX version 2 7 238...
Page 277: ...Appendix E Replication Overview 259 Snap Assisted Replication Navigating with ManageTrends...
Page 281: ...Appendix E Replication Overview 263 Replication SAR view Primary Box SAR view Secondary Box...
Page 285: ...Appendix E Replication Overview 267 After Failover Operation in Secondary Box...
Page 300: ...StorTrends 1300 User s Guide StorTrends iTX version 2 7 282...
Page 308: ...StorTrends 1300 User s Guide StorTrends iTX version 2 7 290...
Page 330: ...StorTrends 1300 User s Guide StorTrends iTX version 2 7 312...
Page 356: ...StorTrends 1300 User s Guide StorTrends iTX version 2 7 338...