Industry Cellular Gateway
3.5.4 Issue Certificate
When you have a Certificate Signing Request (CSR) that needs to be certificated by the root CA of the device,
you can issue the request here and let Root CA sign it. There are two approaches to issue a certificate. One is
from a CSR file importing from the managing PC and another is copy-paste the CSR codes in gateway’s web-
based utility, and then click on the "Sign" button.
If the gateway signs a CSR successfully, the "Signed Certificate View" window will show the resulted certificate
contents. In addition, a "Download" button is available for you to download the certificate to a file in the
managing PC.
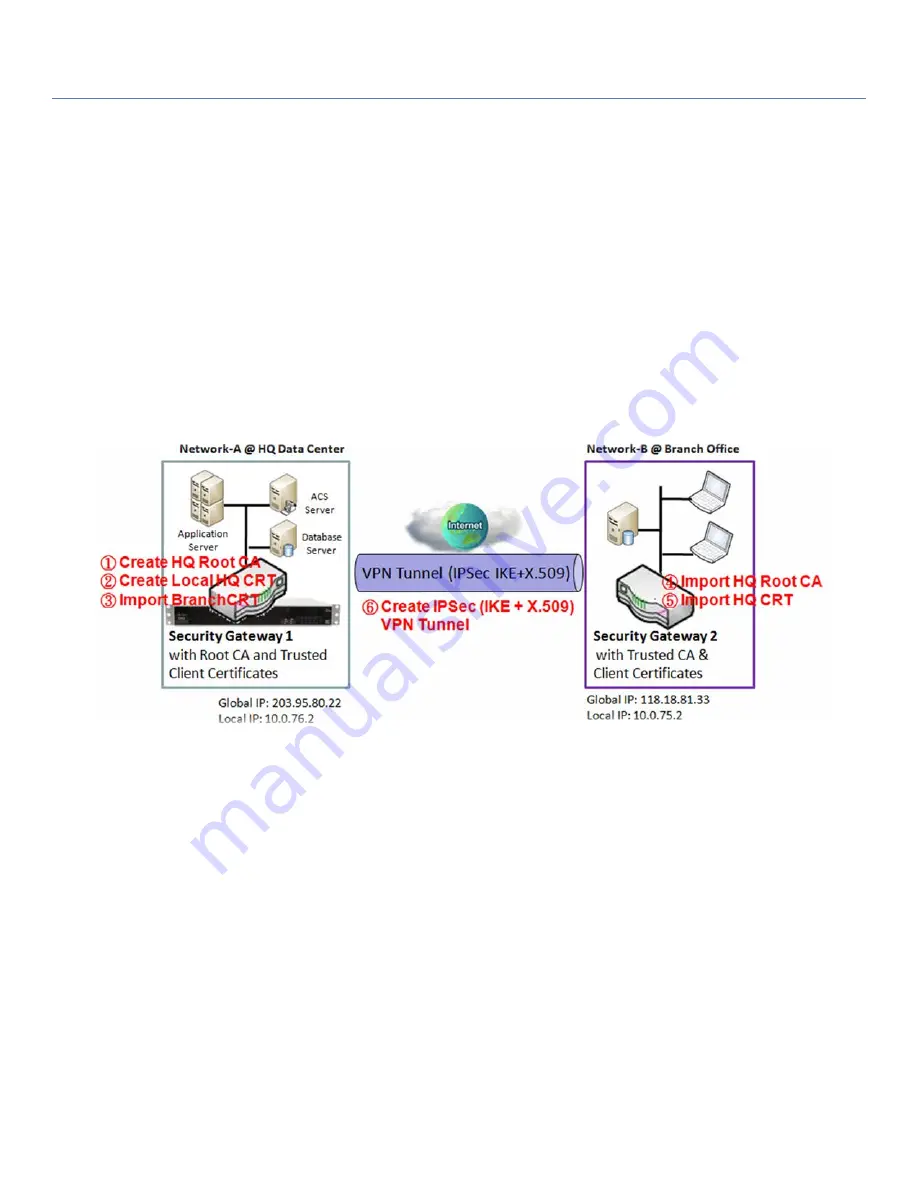
Self-signed Certificate Usage Scenario
Scenario Application Timing (same as the one described in "My Certificate" section)
When the enterprise gateway owns the root CA and VPN tunneling function, it can generate its own
local certificates by being signed by itself. Also imports the trusted certificates for other CAs and
Clients. These certificates can be used for two remote peers to make sure their identity during
establishing a VPN tunnel.
Scenario Description (same as the one described in "My Certificate" section)
Gateway 1 generates the root CA and a local certificate (HQCRT) signed by itself. Also imports a
trusted certificate (BranchCRT) –a BranchCSR certificate of Gateway 2 signed by root CA of Gateway
1.
Gateway 2 creates a CSR (BranchCSR) to let the root CA of the Gateway 1 sign it to be the
BranchCRT certificate. Import the certificate into the Gateway 2 as a local certificate. In addition,
178