1–17
PacketMax 5000 Installation and Operation Manual, 10007678 Rev J
Chapter 1. Overview Of Base Station
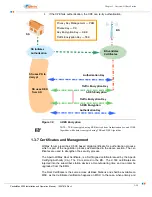
1.3.6 3 DES Encryption
3 DES encryption scheme helps secure the communication channels between the
base station and subscriber station by encrypting the data flow between the two.
The Encryption procedure is as follows:
1.
At first, the SS initiates the authorization process and sends message to the
BS indicating that it is capable of encryption.
2.
The BS authorizes the SS by verifying the device and Vendor Certificate of the
SS during the Privacy Key Management (PKM) Message Exchange.
3.
An Authorization Key (AK) is used to decrypt the Traffic Encryption Keys
(TEKs) using PKM protocol. The AK is periodically refreshed and is encrypted
using 3DES.
4.
In the BS, the TEKs are generated and send to SS using the 3DES encryption
format. The SS decrypts these TEKs using a Key Encryption Key (KEK) gen-
erated from the AK. If the BS encrypts the TEK using the RSA Public Key of
SS, then the SS decrypts it using its Private Key.
5.
The TEKs are used for encrypting data on different Service Flows (SF) between
the BS and SS.
6.
All the Service Flows for one SS will have the same key in both upstream and
downstream.
NOTE: To enable encryption on every service flow, please refer to the WaveCenter
EMS User Manual.
7.
The traffic between the BS and SS can now be encrypted/decrypted using the
TEK keys.
Summary of Contents for PacketMAX 5000
Page 10: ...Preface Preface vi PacketMax 5000 Installation and Operation Manual 10007678 Rev J ...
Page 14: ...Table Of Content TOC 4 PacketMax 5000 Installation and Operation Manual 10007678 Rev J ...
Page 146: ...E 4 PacketMax 5000 Installation and Operation Manual 10007678 Rev J Chapter E Certifications ...
Page 150: ...F 4 PacketMax 5000 Installation and Operation Manual 10007678 Rev J Chapter F Troubleshooting ...