B1.119 Vector Base Address Register
The VBAR characteristics are:
Purpose
Holds the exception base address for exceptions that are not taken to Monitor mode or to Hyp
mode when high exception vectors are not selected.
Usage constraints
This register is accessible as follows:
EL0
(NS)
EL0
(S)
EL1
(NS)
EL1
(S)
EL2 EL3
(SCR.NS = 1)
EL3
(SCR.NS = 0)
-
-
RW
RW RW RW
RW
Software must program the Non-secure instance of the register with the required initial value as
part of the processor boot sequence.
Configurations
If EL3 is using AArch32, there are separate Secure and Non-secure instances of this register.
If EL3 is using AArch32, write access to VBAR(S) is disabled when the
CP15SDISABLE2
signal is asserted HIGH.
The Non-secure VBAR is architecturally mapped to the AArch64 VBAR_EL1 register. See
B2.100 Vector Base Address Register, EL1
The Secure VBAR is mapped to AArch64 register VBAR_EL3[31:0]. See
.
Attributes
VBAR is a 32-bit register.
RES
0
31
0
Vector Base Address
4
5
Figure B1-67 VBAR bit assignments
Vector Base Address, [31:5]
Bits[31:5] of the base address of the exception vectors, for exceptions taken in this exception
level. Bits[4:0] of an exception vector are the exception offset.
[4:0]
Reserved,
RES0
.
To access the VBAR:
MRC p15, 0, <Rt>, c12, c0, 0 ; Read VBAR into Rt
MCR p15, 0, <Rt>, c12, c0, 0 ; Write Rt to VBAR
Register access is encoded as follows:
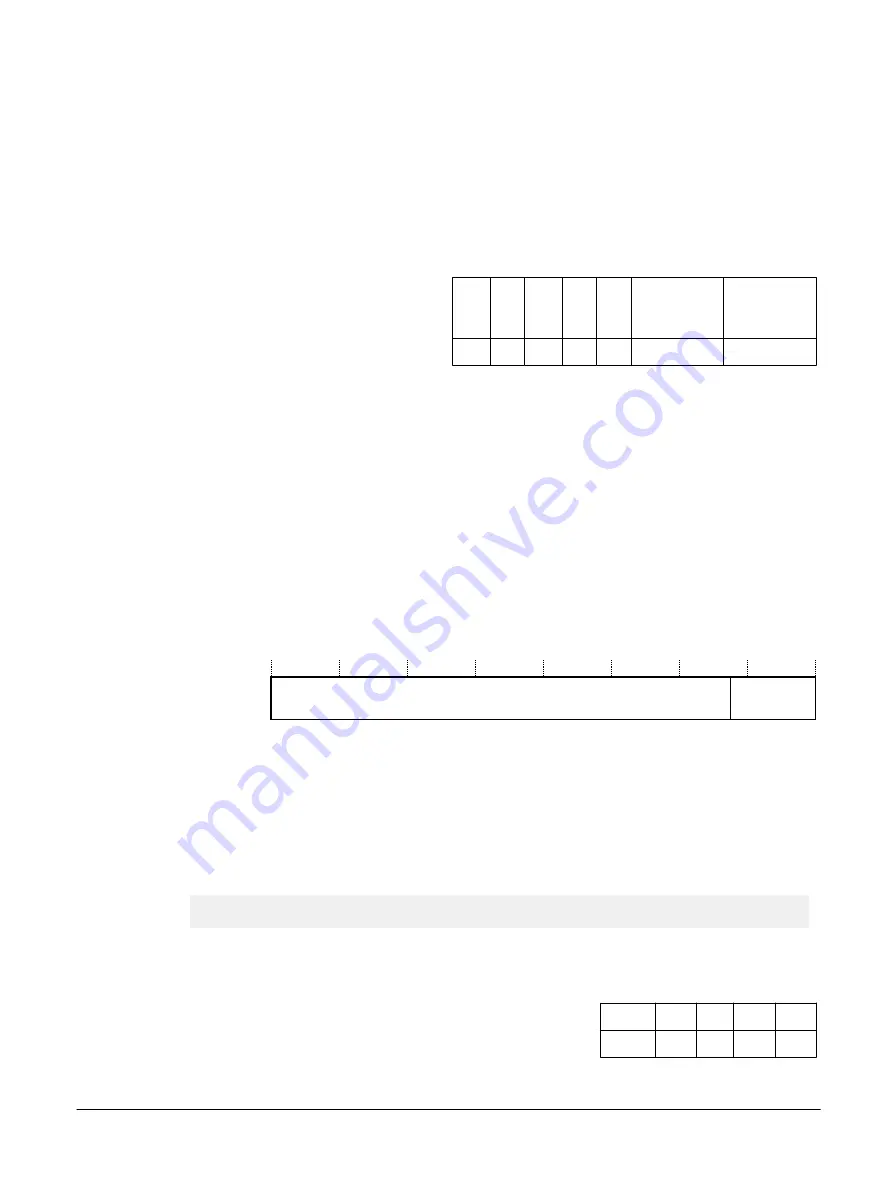
Table B1-98 VBAR access encoding
coproc opc1 CRn CRm opc2
1111
000
1100 0000 000
B1 AArch32 system registers
B1.119 Vector Base Address Register
100236_0100_00_en
Copyright © 2015–2017, 2019 Arm Limited or its affiliates. All rights
reserved.
B1-354
Non-Confidential
Summary of Contents for Cortex-A35
Page 4: ......
Page 18: ......
Page 26: ......
Page 27: ...Part A Functional Description ...
Page 28: ......
Page 145: ...Part B Register Descriptions ...
Page 146: ......
Page 573: ...Part C Debug ...
Page 574: ......
Page 845: ...Part D Appendices ...
Page 846: ......
















































