79
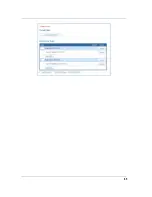
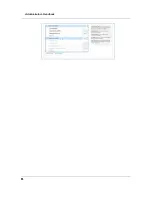
block the most common types of DoS attacks. For special requirements or circumstances, a variety of addi-
tional blocking characteristics is offered. See the following table.
If you make any changes here, click the
Save
Save
Save
Save
button.
Menu item
Function
Drop packets with invalid source or desti-
nation IP address
Whether packets with invalid source or destination IP address(es) are to be
dropped
Protect against port scan
Whether to detect and drop port scans.
Drop packets with unknown ether types
Whether packets with
unknown ether types
are to be dropped
Drop packets with invalid TCP flags
Whether packets with invalid TCP flag settings (NULL, FIN, Xmas, etc.)
should be dropped
Drop incoming ICMP Echo requests
Whether all ICMP echo requests are to be dropped;
On
or
Off
.
Flood Limit
Whether packet flooding should be detected and offending packets be
dropped;
On
or
Off
.
Flood rate limit
Specifies the number limit of packets per second before dropping the
remainder.
Flood burst limit
Specifies the number limit of packets in a single burst before dropping the
remainder.
Flood limit ICMP enable
Whether ICMP traffic packet flooding should be detected and offending
packets be dropped;
On
or
Off
.
Flood limit UDP enable
Whether UDP traffic packet flooding should be detected and offending
packets be dropped;
On
or
Off
.
Flood limit UDP Pass multicast
Allows exclusion of UDP multicast traffic.
On
by default.
Flood limit TCP enable
Allows exclusion of TCP traffic.
Off
by default.
Flood limit TCP SYN-cookie
Allows TCP SYN cookies flooding to be excluded.
Neighbor Discovery Attack protection
Prevents downstream traffic from an upstream device that sends excessive
traffic but receives no replies;
On
or
Off
.
ESP Header Forwarding
Allows the use of Encapsulating Security Payload (ESP) data payload encryp-
tion for IP Secure (IPsec) from qualifying endpoints;
On
or
Off
.
Authentication Header Forwarding
Accept and forward IPSec packets with Authencation Headers, which may
be used by some IPSec implementations to validate packet sources ;
On
or
Off
.
Reflexive ACL
When IPv6 is enabled, Reflexive Access Control Lists can deny inbound IPv6
traffic unless this traffic results from returning outgoing packets (except as
configured through firewall rules).
ESP ALG
This feature helps ESP (IPSec encryption), work properly when using NAT.
Can sometimes cause problems for non-NATed hosts (such as devices on the
Public LAN).
SIP ALG
This feature understands the SIP protocol used by the specific application
and does a protocol-packet inspection of traffic through it. A NAT router
with a built in SIP ALG can rewrite information within the SIP messages (SIP
heads and SDP body) making signalling and audio traffic between the client
behind NAT and the SIP endpoint possible.
Summary of Contents for NVG595
Page 10: ...Administrator s Handbook 10 ...
Page 65: ...65 ...
Page 68: ...Administrator s Handbook 68 ...
Page 84: ...Administrator s Handbook 84 The following is an example log portion saved as a TXT file ...
Page 90: ...Administrator s Handbook 90 ...
Page 185: ...185 Please visit http www ARRIS com recycle for instructions on recycling ...
Page 210: ...Administrator s Handbook 210 ...
Page 220: ...Administrator s Handbook 218 ...
Page 224: ...Administrator s Handbook 222 ...
Page 226: ...Administrator s Handbook 224 ...