ClearPass Guest 3.9 | Deployment Guide
Report Management |
345
Match
filters check if a value matches a particular condition, which could be a regular expression or
other match value.
List
filters check to see if a value is found in a list.
Click the
Create output filter
link to create an output filter.
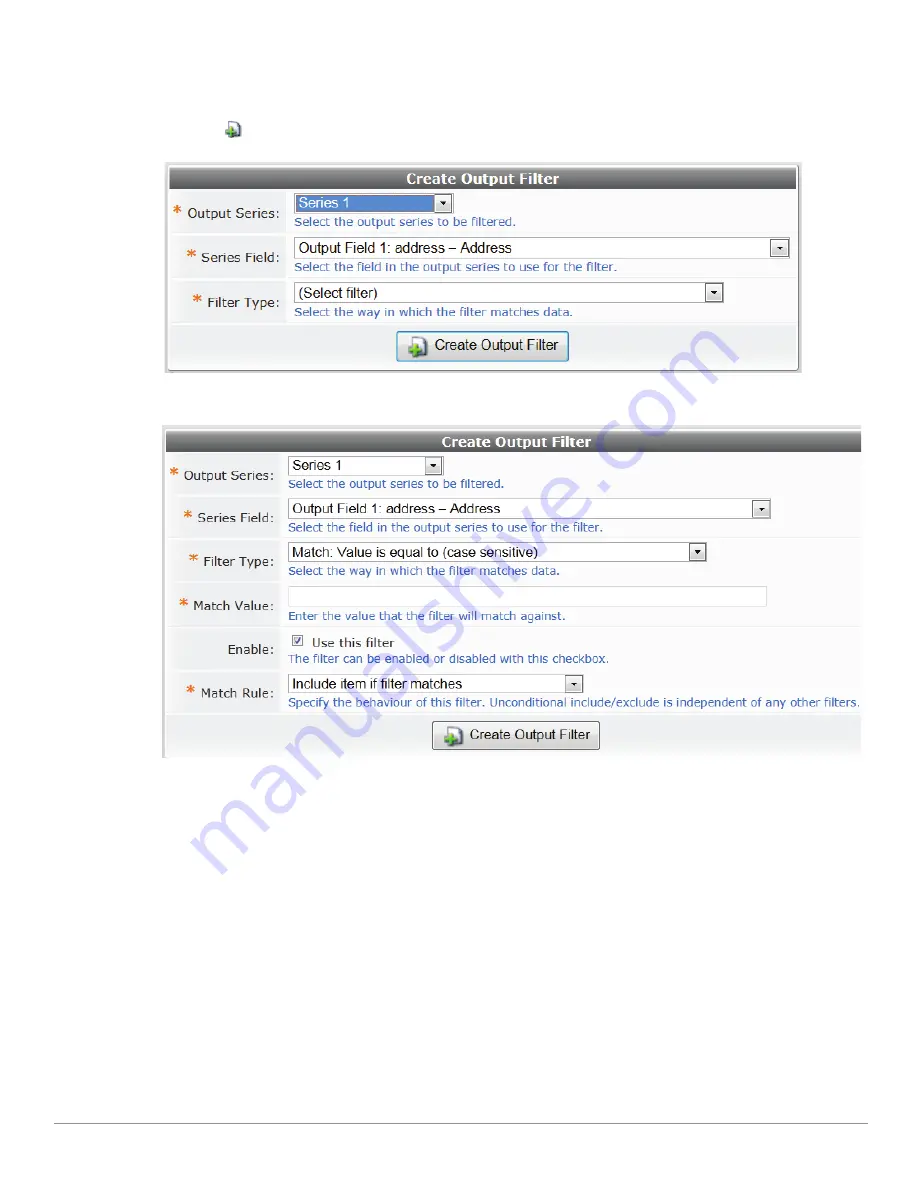
Select the output series you want to filter in order to view the remaining filter options.
You can select any of the source fields that would be available to the output series, or any of the fields in the
output series. This allows output filtering to be performed based on either the report data store, or the
output series data.
The types of output filter that are available are the same as used in the source filters.
See
“Source
Filters”
in this chapter for details about the types of filter that are available.
The Match Rule allows you to construct more complex filtering rules. You can choose from the following
matching rules:
Include item if filter matches
– If the filter matches the item in the output series, the item will be
included. The remaining filters will be applied in order.
Exclude item if filter matches
– If the filter matches the item in the output series, the item will not be
included. The remaining filters will be applied in order.
Unconditionally include item if filter matches
– If the filter matches the item in the output series,
the item will always be included in the output. No further filters will be applied to the data once this
filter has matched.
Summary of Contents for ClearPass Guest 3.9
Page 1: ...ClearPass Guest 3 9 Deployment Guide ...
Page 32: ...32 Management Overview ClearPass Guest 3 9 Deployment Guide ...
Page 178: ...178 RADIUS Services ClearPass Guest 3 9 Deployment Guide ...
Page 316: ...316 Guest Management ClearPass Guest 3 9 Deployment Guide ...
Page 410: ...410 Administrator Tasks ClearPass Guest 3 9 Deployment Guide ...
Page 414: ...414 Administrator Tasks ClearPass Guest 3 9 Deployment Guide ...
Page 423: ...ClearPass Guest 3 9 Deployment Guide Hotspot Manager 423 ...
Page 440: ...440 High Availability Services ClearPass Guest 3 9 Deployment Guide ...
Page 518: ...518 Index ClearPass Guest 3 9 Deployment Guide ...