416
| IAP-VPN Deployment Scenarios
Aruba Instant 6.5.0.0-4.3.0.0 | User Guide
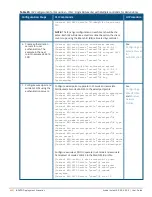
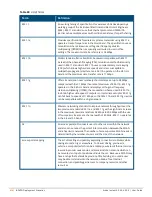
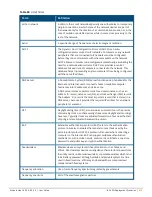
Term
Definition
hotspot
A WLAN node that provides Internet connection and virtual private
network (VPN) access from a given location. A business traveler, for
example, with a laptop equipped for Wi-Fi can look up a local hot spot,
contact it, and get connected through its network to reach the Internet
and their own company remotely with a secure connection. Increasingly,
public places, such as airports, hotels, and coffee shops are providing
free wireless access for customers.
IEEE 802.11 standards
The IEEE 802.11 is a set of standards that are categorized based on the
radio wave frequency and the data transfer rate.
POE
Power over Ethernet (PoE) is a method of delivering power on the same
physical Ethernet wire used for data communication. Power for devices
is provided in one of the following two ways:
l
Endspan— The switch that an AP is connected for power supply.
l
Midspan— A device can sit between the switch and APs
The choice of endspan or midspan depends on the capabilities of the
switch to which the IAP is connected. Typically if a switch is in place and
does not support PoE, midspan power injectors are used.
PPPoE
Point-to-Point Protocol over Ethernet (PPPoE) is a method of connecting
to the Internet typically used with DSL services where the client connects
to the DSL modem.
QoS
Quality of Service (QoS) refers to the capability of a network to provide
better service to a specific network traffic over various technologies.
RF
Radio Frequency (RF) refers to the portion of electromagnetic spectrum
in which electromagnetic waves are generated by feeding alternating
current to an antenna.
TACACS
Family of protocols that handle remote authentication and related
services for network access control through a centralized server.
Derived from TACACS but an entirely new and separate protocol to
handle AAA services. uses TCP and is not compatible with
TACACS. Because it encrypts password, username, authorization, and
accounting, it is less vulnerable than RADIUS.
VPN
A Virtual Private Network (VPN) network that uses a public
telecommunication infrastructure, such as the Internet, to provide
remote offices or individual users with secure access to their
organization's network. A VPN ensures privacy through security
procedures and tunneling protocols such as the Layer Two Tunneling
Protocol ( L2TP ). Data is encrypted at the sending end and decrypted at
the receiving end.
Table 88:
List of Terms