11
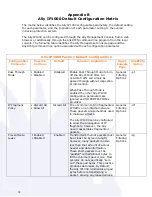
Intrusions Prevented Automatically by Default
Area
Description and Protection
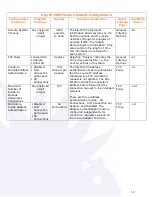
Information Leakage
Previously transmitted data is often used by network cards
to fill in non-required fields or to increase packet sizes to
meet the required minimum frame size of various protocols.
For instance, Ethernet packets must be at least 64 bytes in
length. Packets that are shorter than this required
minimum are padded with a previous transmission’s data to
create a 64 byte packet length. Therefore, confidential
information on the inside of your LAN that has been
accessed correctly, and without encryption, can be sent out
to the Internet on the next DNS resolution request, as one
example. ALLY IP1000 changes the content of all bytes
beyond the exact size required, or within non-required
fields, in order to prevent data leakage.
Network
Reconnaissance:
IP Address Discovery;
TCP Port Discovery;
UDP Port Discovery;
OS Fingerprinting
A critical part of an attacker’s network reconnaissance is to
determine what addresses, ports, operating systems and
firewall devices are used in your network. The Ally IP1000
prevents address discovery, port discovery, bounce-
scanning and other types of network recons by default.
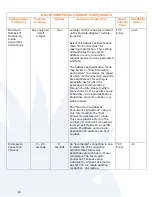
IP Spoofing
Attackers frequently change their packets to show a
different IP address than the one they are actually using.
For connection-oriented sessions, such as HTTP and TCP/IP,
the Ally appliance prevents any connection into the network
unless the original source IP address remains unchanged
throughout the session. For example, only ACK responses
that match the originator’s IP address from the initial SYN
request are allowed into the network.
Resource Flooding &
Denial of Service (DoS)
The Ally IP1000 protects against DoS and its variants along
with illegitimate large amounts of traffic intended to
overload a system to an extent it is unable to respond to
legitimate traffic. Examples of DoS and other resource
floods that are thwarted by the Ally IP1000 are: SYN;
SYN/ACK; ACK; RESET; 3-way connection ‘hogs’
(handshake takes place, but no data sent); Invalid TCP
packets; and Open Idle Connections.
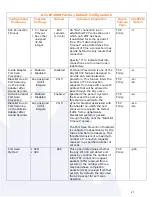
Session Hijacking:
Initial Sequence Number
(ISN) Guessing;
IPID Guessing
Session hijacking involves brute force methods to attempt
to match an existing ISN, IPID, and other fields within the
IP and TCP header. By default, the Ally IP1000 hardens,
encrypts and randomizes many of the IP and TCP fields to
prevent session hijacking. Windows XP nodes sitting behind
a typical firewall have a 12% likelihood of being hijacked.
With an Ally IP1000 in place, this likelihood drops to a
0.00001% chance of success.
Worm Mitigation
Worms typically propagate by scanning for the next target
victim. The Ally IP1000 detects these scans and blacklists
the offending node and drops any further traffic from that
node. Therefore, worm propagation is stopped from coming
into your network by default.
Summary of Contents for ALLY IP1000
Page 1: ...User Guide...
Page 34: ......