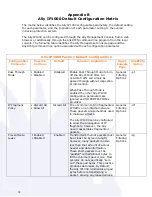
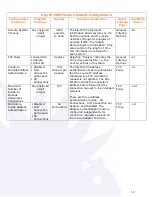
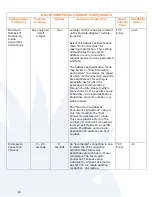
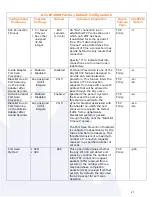
31
License Agreement for Embedded Software
And Notice of Third Party Software
THIS AGREEMENT (the “Agreement”) CONSTITUTES A LEGAL AGREEMENT BETWEEN THE PURCHASER OF THIS
HARDWARE (“You”), AND ARXCEO CORPORATION (“ARXCEO”) REGARDING THE SOFTWARE EMBEDDED IN THE
HARDWARE OR OTHERWISE INSTALLED ON THE HARDWARE AS DELIVERED. YOU SHOULD CAREFULLY READ THE
FOLLOWING TERMS AND CONDITIONS BEFORE OPENING THIS PACKAGE. OPENING THIS PACKAGE WILL BE CONSTRUED AS
YOUR ACCEPTANCE OF THESE TERMS AND CONDITIONS. IF YOU DO NOT AGREE TO THEM, PROMPTLY RETURN THE UNOPENED
PACKAGE FOR A REFUND. USE OF THE EMBEDDED SOFTWARE OUTSIDE OF THIS AGREEMENT CONSTITUTES A VIOLATION OF
U.S. AND INTERNATIONAL COPYRIGHT LAW.
1. Grant of License: ARXCEO grants to you a limited, revocable license of the ARXCEO software and/or firmware (the
“Software”) that is embedded in or otherwise installed as delivered on the enclosed hardware (the “Equipment”), solely as the
Software is installed at the date of purchase, and solely on the Equipment at one site; such license is strictly limited to use of the
Software, in an unmodified state, on the unmodified Equipment. From time to time, ARXCEO may, in its sole discretion, provide
upgraded software for replacement of the Software and/or Third Party Products (as defined in Section 5) in connection with the
Equipment (an “Upgrade”). Each Upgrade is governed by the terms set forth in ARXCEO’s distribution materials (e.g., the terms
presented on ARXCEO’s web page linking to the upgrade, if provided by Internet download, or the terms of any documentation
accompanying physical media distribution, if any) associated with that specific Upgrade (the “Upgrade Materials”), which may list
specific models of equipment or specific purchase plans to which the Upgrade is made available or licensed. You understand and
agree that use of an Upgrade shall be governed by the license in the Upgrade Materials associated with such Upgrade (the
Upgrade License); that this agreement does not grant any rights in, create any expectation of, and does not otherwise cover any
Upgrade; and that because this license gives you no rights in any Upgrade, use of an Upgrade with equipment not specified in the
Upgrade License or otherwise outside the scope of the Upgrade License is a violation of copyright in that Upgrade.
2. Copy Restrictions/Ownership of Software. The Software is licensed, not sold. Your rights in the Equipment are subject to
the terms of your purchase or leasing arrangement therefore, and do not in any way enlarge or imply rights in the Software; in all
cases, ARXCEO retains title to the Software including any and all copies (whether authorized or not), regardless of form or media,
and to all copyrights therein. The Software and accompanying written materials are copyrighted. You may make one copy of the
Software (the “Backup Copy”) solely for backup and archival purposes, which copy must be held in strict confidentiality, and may
not be transferred except together with the Equipment. You agree not to make any copy other than the single first-generation
Backup Copy. You agree not to extract the Software or any portion thereof to other media (other than the making of the Backup
Copy), upload the Software or any portion thereof to any equipment (other than the restoration of the Backup Copy to the
Equipment in an unmodified state), or modify the Software in any manner.
3. Transfer and Other Restrictions. You may transfer the Software only both (a) with a copy of this Agreement, and (b) as
installed on the Equipment, which transfer may be made to another party only on a permanent basis and only if the other party
accepts the terms and conditions of this Agreement. Upon such transfer, you must transfer all accompanying written materials,
and either transfer or destroy all copies of the Software. Any transfer or attempted transfer in violation of this provision is void.
You may not lease, rent, merge, time share, or use the Software in the operation of any service bureau. You agree not to reverse
engineer, decompile or disassemble the Software, except to the extent you are permitted to do so by applicable law that cannot be
waived by this Section 3. You may not use the Software for or in connection with any purpose or activity that (i) violates or
infringes upon the rights of any others (including without limitation the right of privacy or the right of publicity, copyright, and
trade secret), (ii) may be illegal, abusive, profane, obscene, immoral, indecent, threatening, slanderous, libelous, scandalous, or
offensive to an average person, (iii) violates any law, regulation, or regulatory advisory, opinion, including particularly without
limitation, those in the areas of antitrust, fair trade and securities law, or medical information (by way of non-limiting example,
HIPAA requirements), or (iv) involves or relates to operation of nuclear facilities, aircraft navigation, aircraft communication,
aircraft flight control, devices or systems in which serious injury or death to the operator of the device or system, or to others due
to a malfunction (including, without limitation, software related delay or failure) could reasonably be foreseen. You shall be
responsible to ensure compliance with the foregoing.
4. Termination. The licenses and rights granted in connection with this Agreement are effective for the operational life of the
unmodified Equipment or until earlier terminated. The Agreement will terminate if you fail to comply with any provision of this
Agreement, such termination to be automatically effective without notice except to the extent that notice is required by non-
waivable provision of law, in which case the termination shall be effective immediately upon such notice as the law shall require.
You may voluntarily terminate at any time. Upon termination, you agree to destroy or purge all copies of the Software and
accompanying written materials. You acknowledge and agree that upon termination of this Agreement, any attempt to access or
use the Software is prohibited and unauthorized, and you agree that you will not make any such attempts. The provisions of
Sections 3, 4, 5, 8, 9, 10, and 11 shall survive any termination of this Agreement.
5. ARXCEO’s Licensors and Third Party Software: In addition to the Software, the Equipment includes the following
software programs and code that are owned by ARXCEO’s licensors, respectively (“Third Party Products”): the Microsoft XP
Embedded program (“MSXPE”), licensed from Microsoft Corporation (“MS”) and subject to the MS EULA Attached as Schedule A;
Apache Tomcat (“Tomcat”), licensed by Apache (“Apache”) under the ASF Apache License version 2.0, Attached as Schedule B;
and possibly other code received by ARXCEO as “free software” without restrictions. The Third Party Products are provided as a
convenience to You, and are not considered part of the Software. Your license to MSXPE is your sole source of license, rights,
remedies, warranties, and benefits related to MSXPE. You agree to all of the terms of the MS EULA, and agree with ARXCEO that
you will comply with all such terms. Your license to the remaining Third Party Products is directly with and from Apache or the
other licensors thereof, and you agree to comply with the terms of such licenses. In addition to the terms set forth in the relevant
third party licenses (including without limitation the MS EULA and the Apache license), you agree that all Third Party Products
are subject to all restrictions and obligations on You (but not the rights, remedies, or warranties in Your favor, or the
obligations of ARXCEO) that are set forth in this Agreement for the Software, to the same extent as if the Third Party
Products were considered Software, provided that in the event of a conflict between the terms of this Agreement and the terms of
a Third Party EULA, the Third Party EULA controls, but only with respect to the specific Third Party Product covered under that
Summary of Contents for ALLY IP1000
Page 1: ...User Guide...
Page 34: ......