Asoka® User Guide
PlugLink™ 9760 HD AV Adapter PL9760-ETH
Page 25 of 39
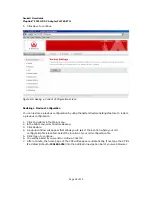
Figure 8-3: System Log View
Some network conditions can produce network traffic that appears to
be an attack, even when no one is deliberately attacking the LAN. To
follow up on a possible attack, contact your ISP to determine the source
of the attack. Regardless of the nature of the attack, your LAN is
protected and no further steps need be taken.
To configure log settings, fill in the form below the log table.
1.
Weekly/Daily/No – Enter how often you would like the system logs to be emailed to you.
2.
Day – Enter the day of the week (like Monday) you would like the system logs to be emailed.
3.
Time – Enter the time you would like the system logs to be emailed.
4.
Email Address – Enter your full email address (
username@mydomain.com
) in the Email
Address field to receive the event log via email. Once sent, the log is cleared from the
gateway memory. If this field is left black, the log is not emailed.
5.
SMTP Address – To email logs, enter the name or IP address of your SMTP server. If this field is
left blank, logs are not emailed.
6.
SMTP Account – Enter the email account ID.
7.
SMTP Password – Enter the password to your email account.