Chapter 9
iPBX30 User Manual
68
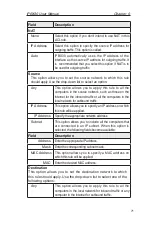
Field
Description
S Y N / I C M P /
UDP Flooding
Check or un-check this option to enable or disable the
logging for SYN/ICMP/UDP flooding attacks. These attacks
involve sending lots of TCP SYN/ICMP/UDP to a host in a
very short period. iPBX30 will not drop the flooding packets
to avoid affecting the normal traffic.
T C P X M A S /
NULL/ FIN Scan
A hacker may be scanning your system by sending these
specially formatted packets to see what services are
available. Sometimes this is done in preparation for a
future attack, or sometimes it is done to see if your system
might have a service, which is susceptible to attack.
XMAS scan:
A TCP packet has been seen with a
sequence number of zero and the FIN, URG, and PUSH
bits are all set.
NULL scan:
A TCP packet has been seen with a
sequence number of zero and all control bits are set to
zero.
FIN scan:
A hacker is scanning the target system using
a “stealth” method. The goal of the hacker is to find out if
they can connect to the system without really connecting
using the “FIN” scanning. It attempts to close a non-
existent connection on the server. Either way, it is an error,
but systems sometimes respond with different error results
depending upon whether the desired service is available or
not.
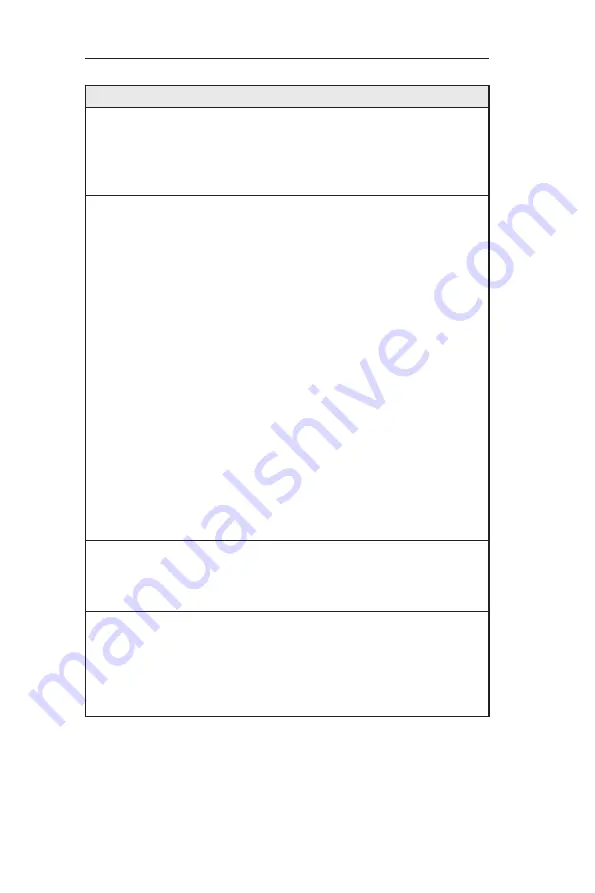
Re-assembly
In the teardrop attack, the attacker’s IP puts a confusing
offset value in the second or later fragment. If the receiving
operating system does not have a plan for this situation, it
can cause the system to crash.
WinNUKE
Check or un-check this option to enable or disable
protection against Winnuke attacks. Some older versions
of the Microsoft Windows OS are vulnerable to this attack.
If the computers in the LAN are not updated with recent
versions/patches, you are advised to enable this protection
by checking this check box.
Summary of Contents for iPBX30
Page 1: ...iPBX30 User Manual E2883 December 2006 ...
Page 151: ......