CHAPTER 5: SYSTEM TAB
MDU Solutions
®
– UCrypt
®
Monitoring Server - Operation Manual
5-9
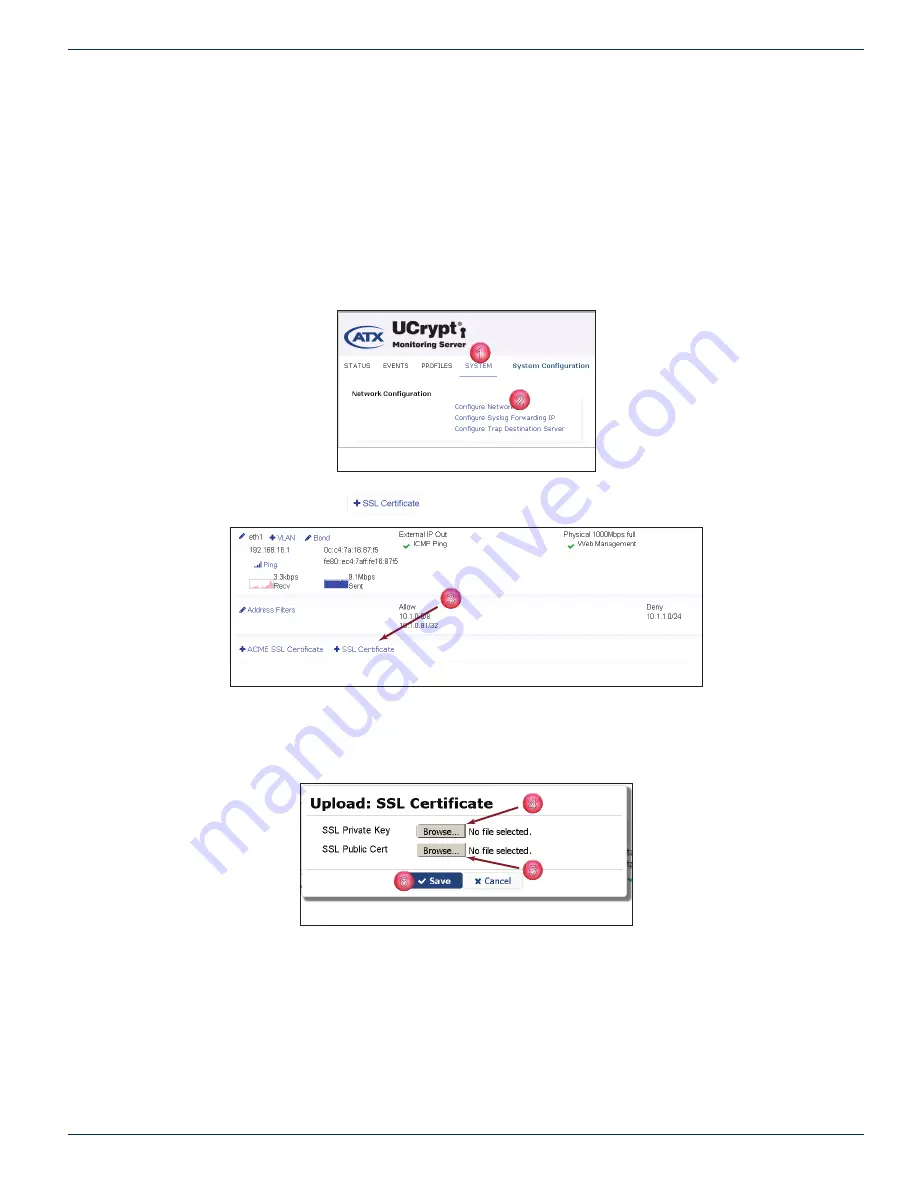
5 .2 .7 Install SSL Certifi cate
SSL (Secure Sockets Layer) Certifi cates are small data fi les that digitally bind a cryptographic key to an organization’s details.
When installed on a secure web server such as the UCrypt Monitoring Server, it activates the padlock and the https protocol
and allows secure connections from the Server to a browser. Once a secure connection is established, all traffi c between the
server and the web browser will be secure. This tool allows the installation of your own self signed SSL certifi cates. This is
useful if you already have an internally trusted self signing authority.
Procedure
This procedure explains how to install an SSL Certifi cate.
1. Click the
System
Tab, Figure 5-22.
2. Click
Confi gure
under
Network Confi guration
section.
3. Click the
+ SSL Certifi cate
button, Figure 5-23.
4. To upload an SSL Private Key, click the Private Key
Browse
button, Figure 5-24.
5. To upload an SSL Public Certifi cate, click the Public Certifi cate
Browse
button.
6. Click
Save
.
1
2
Figure 5-22: Confi gure Network
3
Figure 5-23: Add SSL Certifi cate
4
5
6
Figure 5-24: Upload Certifi cate Files















































