Version 6.2
287
February 2011
SIP User's Manual
3. Web-Based Management
8.
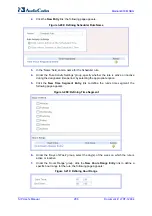
Enter the desired start and end time values for the rule.
Note:
The defined start and end time is applied to all days of the week that you
selected previously.
9.
Click
OK
to return to the previous page, and then click
OK
again to return to the main
page.
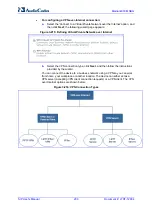
3.3.3.9 Configuring Network Connections
The device supports various network connections, both physical and logical. The
Data
System > Connections
item enables you to configure the various parameters for your
physical connections, the LAN and WAN, and create new connections, using tunneling
protocols over existing connections such as PPP and VPN.
Every network connection in the device can be configured as one of three types: WAN,
LAN or DMZ (Demilitarized). For example, you may define that a LAN connection on the
device operates as a WAN network. This means that all hosts in this LAN are referred to as
WAN computers, both by computers outside the device and by the device itself. WAN and
firewall rules may be applied, such as on any other WAN network. Another example is that
a network connection can be defined as a DMZ network. Although the network is physically
inside the device, it functions as an unsecured, independent network for which the device
merely acts as a router.
Note:
When defining a network connection as a DMZ network:
•
Change the connection's routing mode to 'Route'.
•
Add a routing rule on your external gateway (which may be with your
ISP) informing of the DMZ network behind the device.
You can configure the following network connections:
WAN – Internet connection:
•
Point-to-Point Protocol over Ethernet
•
Ethernet Connection
•
Point-to-Point Tunneling Protocol
•
Layer 2 Tunneling Protocol
•
Dynamic Host Configuration Protocol
•
Manual IP Address Configuration
Virtual Private Network over the Internet:
•
Layer 2 Tunneling Protocol over Internet Protocol Security
•
Layer 2 Tunneling Protocol Server
•
Point-to-Point Tunneling Protocol Virtual Private Network
•
Point-to-Point Tunneling Protocol Server
•
Internet Protocol Security
Summary of Contents for Mediant 800 MSBG
Page 2: ......
Page 366: ...SIP User s Manual 366 Document LTRT 12804 Mediant 800 MSBG Reader s Notes ...
Page 372: ...SIP User s Manual 372 Document LTRT 12804 Mediant 800 MSBG Reader s Notes ...
Page 390: ...SIP User s Manual 390 Document LTRT 12804 Mediant 800 MSBG Reader s Notes ...
Page 404: ...SIP User s Manual 404 Document LTRT 12804 Mediant 800 MSBG Reader s Notes ...
Page 616: ...SIP User s Manual 616 Document LTRT 12804 Mediant 800 MSBG Reader s Notes ...
Page 636: ...SIP User s Manual 636 Document LTRT 12804 Mediant 800 MSBG Reader s Notes ...
Page 652: ...SIP User s Manual 652 Document LTRT 12804 Mediant 800 MSBG Reader s Notes ...
Page 886: ...SIP User s Manual 886 Document LTRT 12804 Mediant 800 MSBG Reader s Notes ...