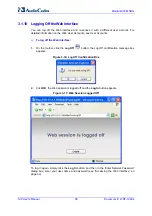
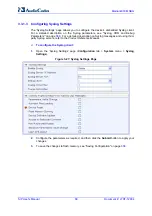
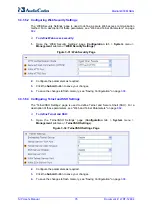
Version 6.2
71
February 2011
SIP User's Manual
3. Web-Based Management
-----BEGIN CERTIFICATE-----
MIIDkzCCAnugAwIBAgIEAgAAADANBgkqhkiG9w0BAQQFADA/MQswCQYDVQQGEwJGUj
ETMBEGA1UEChMKQ2VydGlwb3N0ZTEbMBkGA1UEAxMSQ2VydGlwb3N0ZSBTZXJ2ZXVy
MB4XDTk4MDYyNDA4MDAwMFoXDTE4MDYyNDA4MDAwMFowPzELMAkGA1UEBhMCRlIxEz
ARBgNVBAoTCkNlcnRpcG9zdGUxGzAZBgNVBAMTEkNlcnRpcG9zdGUgU2VydmV1cjCC
ASEwDQYJKoZIhvcNAQEBBQADggEOADCCAQkCggEAPqd4MziR4spWldGRx8bQrhZkon
WnNm`+Yhb7+4Q67ecf1janH7GcN/SXsfx7jJpreWULf7v7Cvpr4R7qIJcmdHIntmf7
JPM5n6cDBv17uSW63er7NkVnMFHwK1QaGFLMybFkzaeGrvFm4k3lRefFhJ
gHYezYHf44LvPRPAq3o8pWDguJuZDIULPwvRw==
-----END CERTIFICATE-----
7.
In the 'Certificates Files' group, click the
Browse
button corresponding to 'Send Server
Certificate...', navigate to the cert.txt file, and then click
Send File
.
8.
After the certificate successfully loads to the device, save the configuration (see
''Saving Configuration'' on page
) and restart the device; the Web interface uses
the provided certificate.
9.
If the device was originally operating in HTTPS mode and you disabled it in Step 2,
then return it to HTTPS by setting the parameter 'Secured Web Connection (HTTPS)'
to 'HTTPS Only' (1) - see ''Configuring Web Security Settings'' on page
Notes:
•
The certificate replacement process can be repeated when necessary
(e.g., the new certificate expires).
•
It is possible to use the IP address of the device (e.g., 10.3.3.1) instead
of a qualified DNS name in the Subject Name. This is not recommended
since the IP address is subject to changes and may not uniquely identify
the device.
•
The server certificate can also be loaded via
ini
file using the parameter
HTTPSCertFileName.
3.3.1.5.2 Client Certificates
By default, Web servers using SSL provide one-way authentication. The client is certain
that the information provided by the Web server is authentic. When an organizational PKI is
used, two-way authentication may be desired: both client and server should be
authenticated using X.509 certificates. This is achieved by installing a client certificate on
the managing PC, and loading the same certificate (in base64-encoded X.509 format) to
the device's Trusted Root Certificate Store. The Trusted Root Certificate file should contain
both the certificate of the authorized user and the certificate of the CA.
Since X.509 certificates have an expiration date and time, the device must be configured to
use NTP (see ''Simple Network Time Protocol Support'' on page
) to obtain the current
date and time. Without the correct date and time, client certificates cannot work.
¾
To enable two-way client certificates:
1.
Set the parameter 'Secured Web Connection (HTTPS)' to 'HTTPS Only' (0) in
''Configuring Web Security Settings'' on page
to ensure you have a method of
accessing the device in case the client certificate doesn’t work. Restore the previous
setting after testing the configuration.
2.
Open the ‘Certificates Signing Request' page (see ''Server Certificate Replacement''
on page
Summary of Contents for Mediant 800 MSBG
Page 2: ......
Page 366: ...SIP User s Manual 366 Document LTRT 12804 Mediant 800 MSBG Reader s Notes ...
Page 372: ...SIP User s Manual 372 Document LTRT 12804 Mediant 800 MSBG Reader s Notes ...
Page 390: ...SIP User s Manual 390 Document LTRT 12804 Mediant 800 MSBG Reader s Notes ...
Page 404: ...SIP User s Manual 404 Document LTRT 12804 Mediant 800 MSBG Reader s Notes ...
Page 616: ...SIP User s Manual 616 Document LTRT 12804 Mediant 800 MSBG Reader s Notes ...
Page 636: ...SIP User s Manual 636 Document LTRT 12804 Mediant 800 MSBG Reader s Notes ...
Page 652: ...SIP User s Manual 652 Document LTRT 12804 Mediant 800 MSBG Reader s Notes ...
Page 886: ...SIP User s Manual 886 Document LTRT 12804 Mediant 800 MSBG Reader s Notes ...