Copyright (c) Fire4 Systems Inc, 2019. All rights reserved
2
AUTHONET FIREWALL OVERVIEW AND OPERATION MANUAL
Contents
PART 1: INTRODUCTION TO THE AUTHONET FIREWALL
Problems with Conventional Firewalls
Dangers from Hackers
Hackers pose two major threats to computer networks
Using The Authonet Firewall
Applications for the Authonet Firewall
PART 2: INSTALLING AND CONFIGURING THE AUTHONET FIREWALL
Network Installation of the Authonet firewall
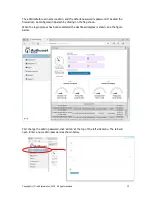
Login as the Administrator
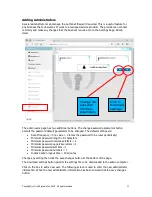
Adding Administrators
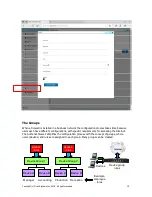
The Groups
What is a Device? it has a MAC address and has requested an IP address
What is a Rule? it can be open access to the Internet or access to specific websites
The Overview Tree: graphic representation of the groups and associated devices and
rules
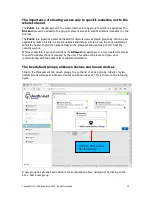
The importance of allowing access only to specific websites, not to the whole Internet
The two default groups, unknown devices and known devices
Simplest firewall configuration
Adding device information
Adding rules to the Known device group
Creating New Device Groups
Creating New Access Rules
Settings: Adding inbound access from the Internet - Port Forwarding
Settings: Adding inbound access from the Internet - DMZ
Settings: Network, LAN port configuration
Settings: Network, WAN port configuration
Settings: Network, 1:1 NAT
Settings: Network, WAN DNS IP
Settings: DNS Management