Copyright (c) Fire4 Systems Inc, 2019. All rights reserved
29
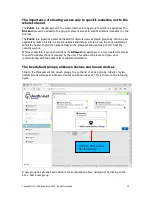
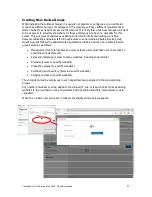
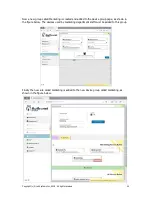
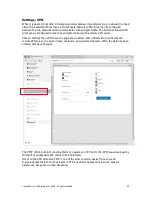
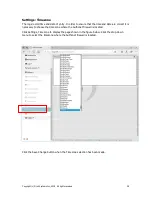
Settings: Network, 1:1 NAT
NAT is Network Address Translation, and is a method of mapping a range of network addresses
onto a different range of network addresses. NAT or NAT'ing is a basic function of a network
router.
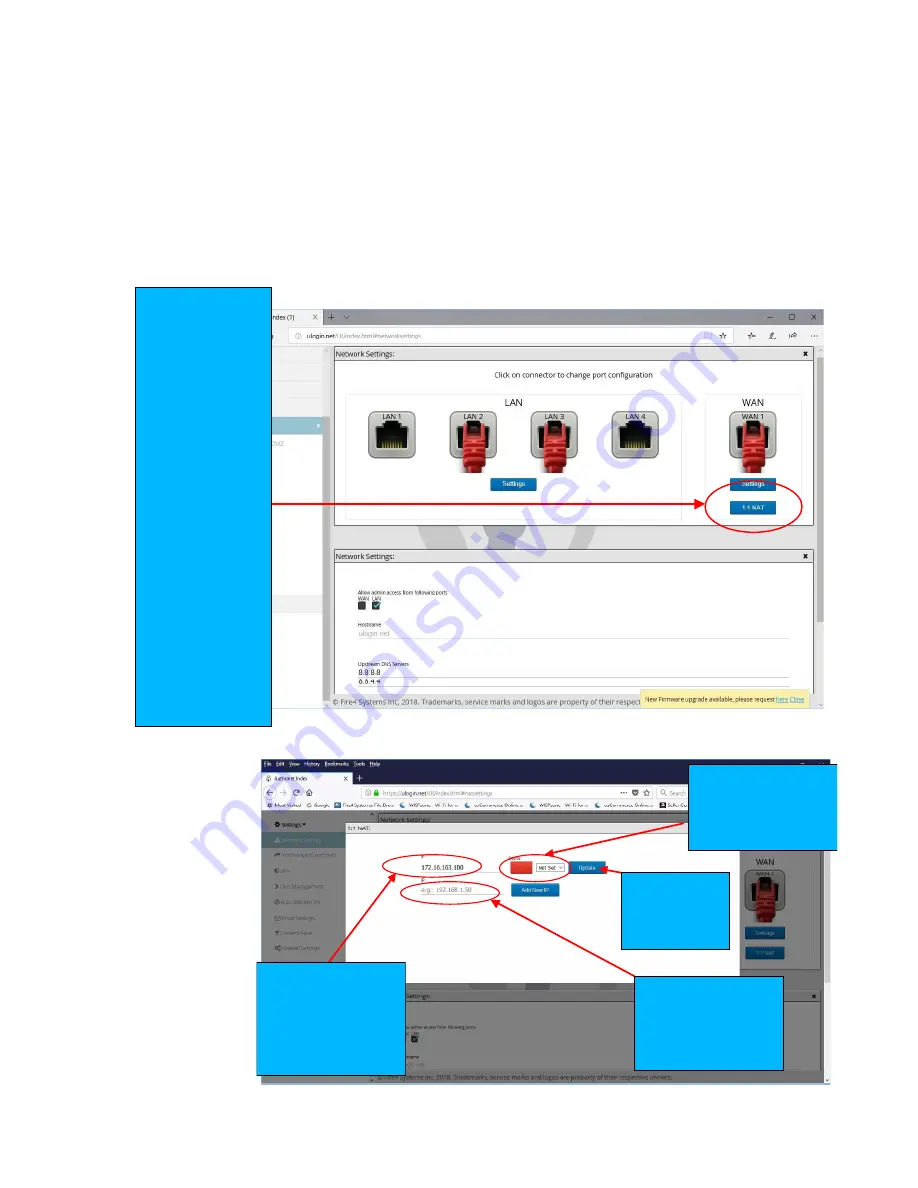
1:1 NAT is a special case of NAT'ing where one IP address in the local area network is mapped to
an IP address in the WAN network. The purpose of this is to make a device on the WAN side of
the network visible to devices on the LAN side of the network. To configure 1:1 NAT'ing, click on
the 1:1 NAT button, as shown in the figure below.
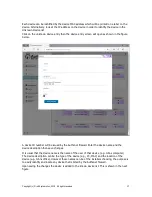
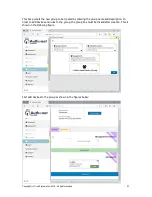
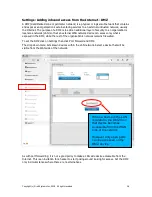
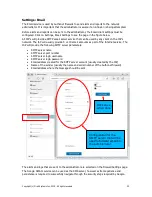
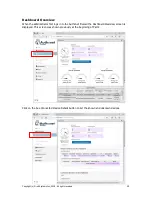
When the 1:1
NAT button is
clicked the
figure will be
seen.
Follow the
sequence of
instructions
shown in the
figure to
configure the
1:1 NAT. A
number of IP
addresses can
be added.
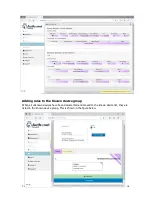
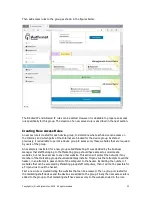
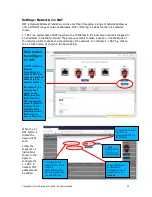
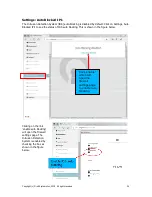
Click button
to configure
1:1 NAT
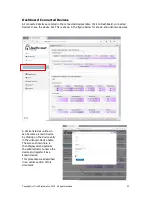
1:1 NAT (Network
Address
Translation) is a
mode of NAT that
maps one internal
address to one
external address
For example, if a
network has a
server on the
WAN side of the
firewall then 1:1
NAT can map the
server IP (alias) to
a device on the
LAN side of the
firewall to permit
the device to
access the server
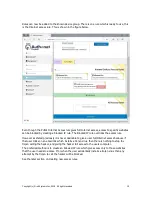
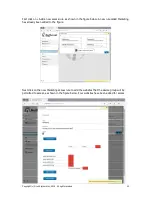
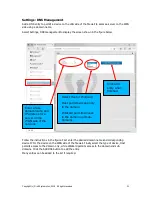
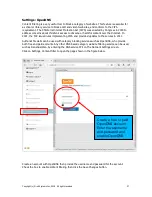
4. Add additional
WAN side IP
addresses here to
associate other
devices
1. Enter a public
alias IP here, the IP
must be
addressable within
the same subnet as
the F10 WAN IP
2. Select the device
that will be
associated with the
WAN alias
3. Click
update when
the data has
been entered