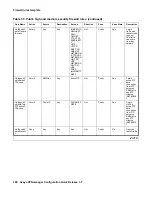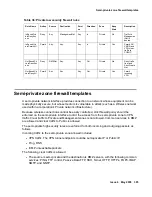
Semi-private zone firewall templates
Issue 4 May 2005
307
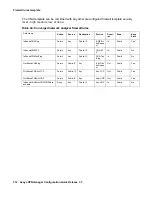
OutBoundS
emiPrivate
VPNAcces
s
Permit
SemiPriv
ateIP
PublicIP
Any
IKE_OUT
IPSEC_NAT_T_OUT
AH
ESP
ICMPDestUnreach
Out
SemiP
rivate
No
Permit outgoing
VPN traffic.
OutBoundS
emiPrivate
PermitAll
Permit
Any
Any
Any
Out
SemiP
rivate
Yes
Permit everything
with Keep state.
(For any traffic
initiated from
Private/
ManagementNET)
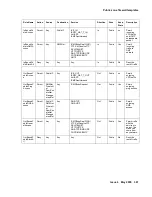
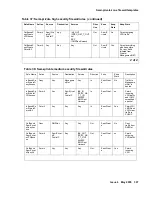
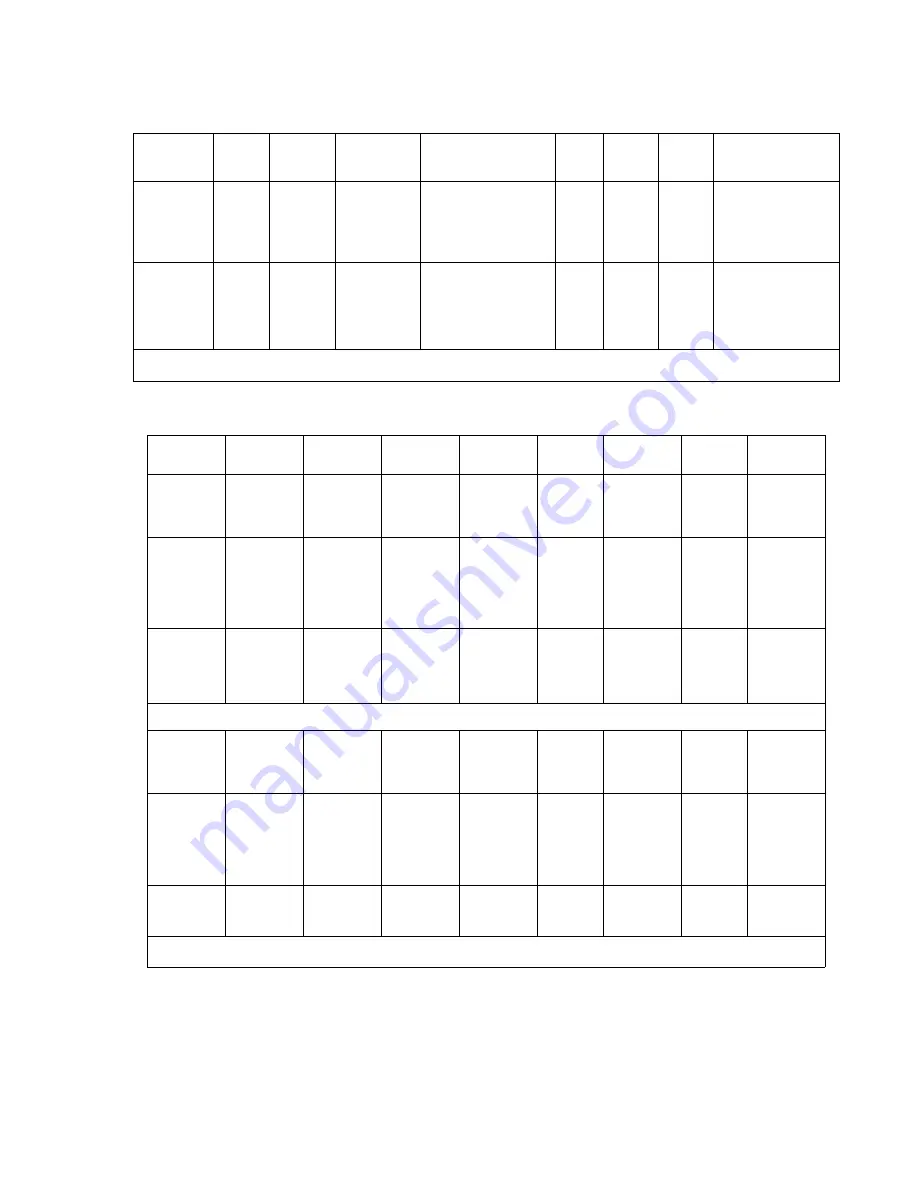
Table 38: Semi-private medium security firewall rules
Rule Name
Action
Source
Destination
Service
Direction
Zone
Keep
State
Description
InBoundSe
miPrivateD
enyAccess
Deny
Any
Manageme
ntNet
Any
In
SemiPrivat
e
No
Traffic to
Manageme
ntNet is
denied.
InBoundSe
miPrivateV
PNAccess
Permit
Any
SemiPrivat
eIP
PublicIP
IKE_IN
IPSEC_NA
T_T_IN
AH/ESP
ICMPDest
Unreach
In
SemiPrivat
e
no
Permit
incoming
VPN traffic
and ICMP
unreachabl
e packet
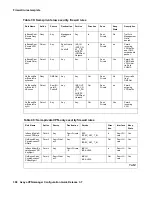
InBoundSe
miPrivateP
ermitAll
Permit
Any
Any
Any
In
SemiPrivat
e
Yes
Permit WI/
VMGR and
VPN, clear
traffic to
PUBLIC
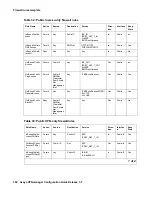
OutBound
SemiPrivat
eDenyAcc
ess
Deny
DMZNet
Any
Any
Out
SemiPrivat
e
No
Deny
traffic from
DMZNet
OutBound
SemiPrivat
eVPNAcce
ss
Permit
SemiPrivat
eIP
PublicIP
Any
IKE_OUT
IPSEC_NA
T_T_OUT
AH/ESP
ICMPDest
Unreach
Out
SemiPrivat
e
no
Permit
outgoing
VPN traffic
OutBound
SemiPrivat
eDenyAll
Permit
Any
Any
Any
Out
SemiPrivat
e
Yes
Permit
incoming
VPN
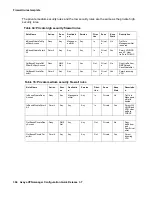
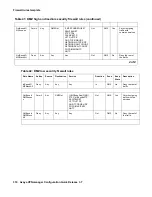
Table 37: Semi-private high security firewall rules (continued)
Rule Name
Action
Source
Destination
Service
Direc
tion
Zone
Keep
State
Keep State
2 of 2
Summary of Contents for 3.7
Page 1: ...VPNmanager Configuration Guide Release 3 7 670 100 600 Issue 4 May 2005...
Page 4: ......
Page 20: ...Preface 20 Avaya VPNmanager Configuration Guide Release 3 7...
Page 32: ...Overview of implementation 32 Avaya VPNmanager Configuration Guide Release 3 7...
Page 53: ...Preferences Issue 4 May 2005 53 Figure 16 Tunnel End Point Policy...
Page 54: ...Using VPNmanager 54 Avaya VPNmanager Configuration Guide Release 3 7...
Page 244: ...Using advanced features 244 Avaya VPNmanager Configuration Guide Release 3 7...
Page 292: ...Upgrading firmware and licenses 292 Avaya VPNmanager Configuration Guide Release 3 7...