Avaya G250 and G250-BRI Branch Office Media Gateways w/FIPS Non-Proprietary Security Policy
Version 1.2 Wednesday, 14 December, 2005
© 2005 Avaya Inc.
May be reproduced only in its original entirety [without revision]. Page 21 of 23
CID 106595
8. Physical Security Policy
8.1.
Physical Security Mechanisms
The multi-chip standalone cryptographic module includes the following physical security
mechanisms:
•
Production-grade components and production-grade enclosure.
8.2.
Operator Required Actions
There are no operator-required actions to maintain physical security.
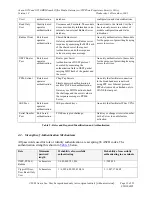
Physical Security Mechanisms
Recommended Frequency of
Inspection/Test
Inspection/Test Guidance Details
Production-grade components and
production-grade enclosure
N/A N/A
Table 8 – Inspection/Testing of Physical Security Mechanisms
9. Mitigation of Other Attacks Policy
The FIPS 140-2 Area 11 requirements are not applicable because the cryptographic
module has not been designed to mitigate specific attacks outside of the scope of FIPS 140-
2.
Other Attacks
Mitigation Mechanism
Specific Limitations
N/A N/A N/A
Table 9 – Mitigation of Other Attacks
10. References
•
For more information on the FIPS 140-2 standard and validation program please see the
NIST website at
http://csrc.nist.gov/cryptval/
•
For more information about Avaya ask your Avaya representative or see
http://www.avaya.com/
•
For more information about Avaya G250 Media Gateway ask your Avaya representative
or see
http://www.avaya.com/gcm/master-usa/en-
us/products/offers/g250_media_gateway.htm