Avaya G250 and G250-BRI Branch Office Media Gateways w/FIPS Non-Proprietary Security Policy
Version 1.2 Wednesday, 14 December, 2005
© 2005 Avaya Inc.
May be reproduced only in its original entirety [without revision]. Page 5 of 23
CID 106595
Roles, Services and Authentication
2
Finite State Model
1
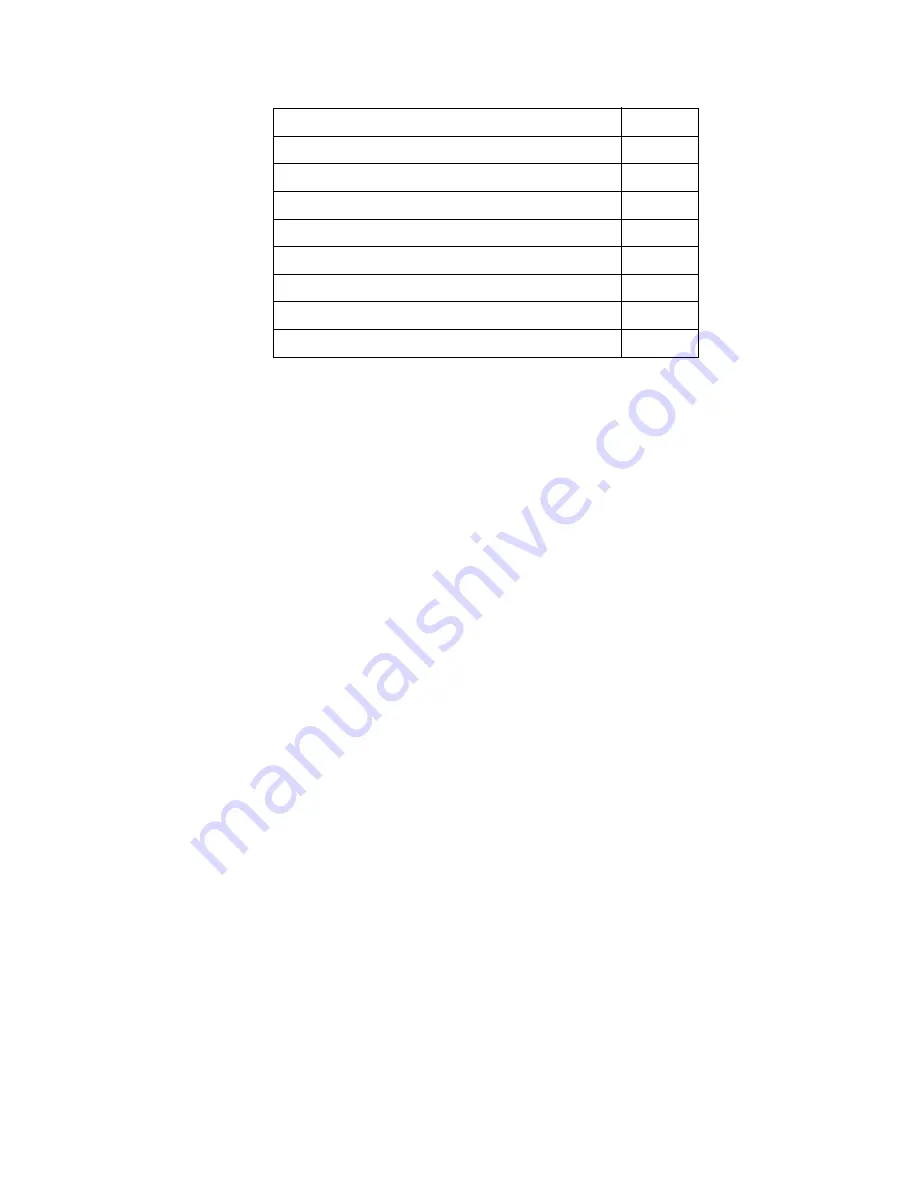
Physical Security
1
Operational Environment
N/A
Cryptographic Key Management
1
EMI/EMC 1
Self-Tests 1
Design Assurance
3
Mitigation of Other Attacks
N/A
Table 1 - Module Security Level Specification
2. Modes of Operation
2.1.
Approved mode of operation
In FIPS mode, the cryptographic module supports the following algorithms:
a.
RSA digital signature verification during firmware upgrades, and license file
authentication. Support for RSA defined in PKCS#1 standard. RSA implementation as
defined by ANSI X9.31 is not supported.
b.
Triple-DES CBC (three key) for IKE encryption and IPSec, and serial number exchange
c.
AES-CBC (128, 192, 256 bit) for IPSec and IKE encryption
d.
SHA-1 for hashing download image digest, license file digest
e.
HMAC SHA-1 for message authentication codes for IKE and IPSEC
f.
DES CBC for encryption of IPSec, and IKE (only supported for communication with
legacy systems) (transitional phase only – valid until May 19, 2007)
g.
Diffie-Hellman key-agreement protocol (groups 2, 5, 14) used to derive IKE and IPSEC
session keys.
The cryptographic module relies on the implemented deterministic random number generator
(DRNG) that is compliant with X9.31 for generation of all cryptographic keys. The non-
deterministic random seed generator is used for the periodic re-seeding of the PRNG.
The cryptographic module may be configured for FIPS mode via execution of the specified
configuration procedure (Section 2.3).
The user can determine if the cryptographic module is running in FIPS vs. non-FIPS mode via
execution of the
show running-config
command through the command-line-interface (CLI), and
verification that the configuration meets the requirements specified in (Section 2.3), and