Avaya G250 and G250-BRI Branch Office Media Gateways w/FIPS Non-Proprietary Security Policy
Version 1.2 Wednesday, 14 December, 2005
© 2005 Avaya Inc.
May be reproduced only in its original entirety [without revision]. Page 6 of 23
CID 106595
•
Use the show system command and verify that “HW ready for FIP: Yes.”
•
Verify that both firmware banks contain firmware images that have been FIPS Approved.
- Use the dir command. The output should show the FIPS Approved versions of the FW
(which can be found at the following URL
http://www.csrc.nist.gov/cryptval/140-
1/140val.all.htm
).
2.2.
Non-FIPS mode of operation
The non-FIPS Approved algorithms implemented by the module are:
a.
Diffie-Hellman (key agreement; key establishment methodology provides between 80–
bits and 112-bits of encryption strength)
b.
MD5
c.
H.248 Link Encryption (use of PTLS and non-compliant AES in non-FIPS mode only,
encryption algorithm)
d.
Avaya Media Encryption (AEA for encryption/decryption)
e.
SSH v2 (use of MD5, DH group 786-2048, non-compliant TDES, non-compliant DES in
non-FIPS mode only, commercially available key establishment protocol)
f.
HMAC-SHA-1 (used in non-compliant manner in SNMPv3 in non-FIPS mode only)
2.3.
Entering FIPS Mode
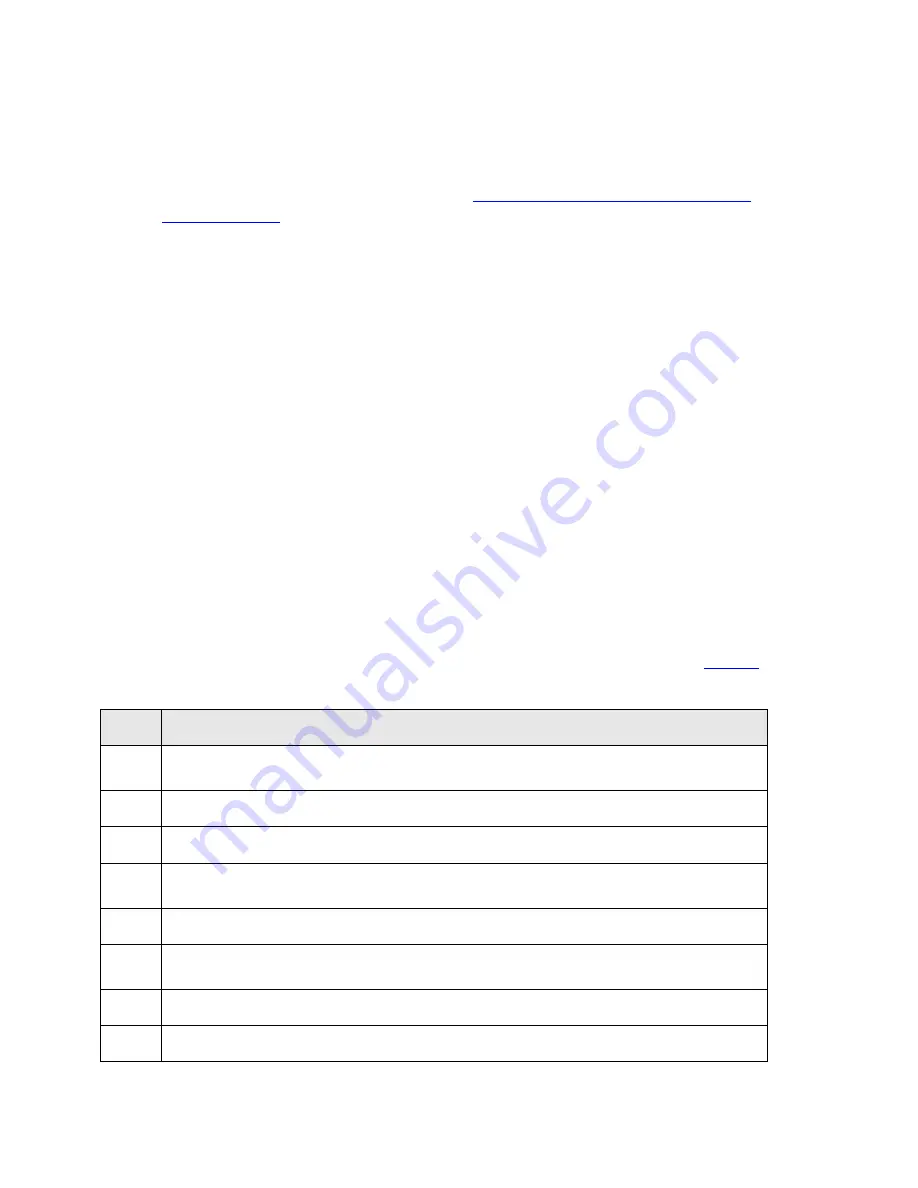
To enter FIPS mode, the Crypto-Officer must follow the procedure outlined in the
Table 2
below.
#
Step Description
1.
Log in to the device as default root/root user acting in Crypto-Officer role, through the local
console port.
2.
Define PMI (Primary Management Interface) interface and execute device reset to activate PMI.
3.
Verify that the HW version of the module is of a FIPS Approved version.
4.
Verify that both firmware image banks contain firmware images, which have been FIPS
Approved.
5.
Verify successful completion of power-up self-tests
6.
If more recent FIPS Approved Gateway image is available download the image using existing
procedures for image download.
7.
If not installed download the Avaya License file with VPN feature activated
8.
Physically disconnect all network interfaces