address which holds the interface index. Packets received over a non-Ethernet interface are
identified with DA address in the format 00:01:00:00:xx and an SA address which holds the
interface index. The
show capture-dummy-headers
command displays the dummy
header addresses and their meaning according to the current configuration.
Note:
Ethernet packets received on a VLAN interface are identified by their VLAN tag. However,
decrypted IPSec packets received on a VLAN interface are stored with a dummy header.
Gxxx-001> show capture-dummy-headers
MAC Description
----------------- ----------------------------------------------------
00:00:01:00:00:01 Decrypted IPSec packet
00:00:0a:00:0a:02 interface fastethernet 10/3
00:00:0c:a0:b0:01 interface vlan 1
00:00:31:00:00:01 interface dialer 1
About simulating packets
Capture lists support the IP simulate command. Refer to
on page 580.
Summary of packet sniffing commands
For more information about these commands, see the
Avaya Branch Gateways G250 and
G350 CLI Reference
.
For more information about these commands, see the
Avaya Branch Gateway G430 CLI
Reference
.
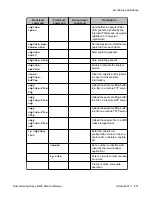
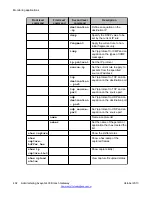
Root level
command
First level
command
Second level
command
Description
capture
buffer-mode
Set the capture buffer to cyclic
mode
capture
buffer-size
Change the size of the capture
file
capture
filter-group
Activate a capture list
capture
interface
Specify a capture interface (by
default, the service captures
from all interfaces
simultaneously)
Monitoring applications
400 Administering Avaya G430 Branch Gateway
October 2013
Summary of Contents for G430
Page 1: ...Administering Avaya G430 Branch Gateway Release 6 3 03 603228 Issue 5 October 2013 ...
Page 12: ...12 Administering Avaya G430 Branch Gateway October 2013 ...
Page 246: ...VoIP QoS 246 Administering Avaya G430 Branch Gateway October 2013 Comments infodev avaya com ...
Page 556: ...IPSec VPN 556 Administering Avaya G430 Branch Gateway October 2013 Comments infodev avaya com ...