AVG 9.0 Email Server Edition © 2009 C opyright AVG Technologies C Z, s.r.o. All rights reserved.
40
The message without its infected or prohibited attachment will be (apart from
the actions selected below) forwarded to the specified e-mail address. This can
be used to verify the correct functioning of the antivirus and/or attachment
filter.
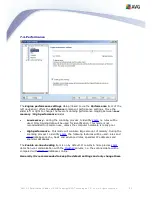
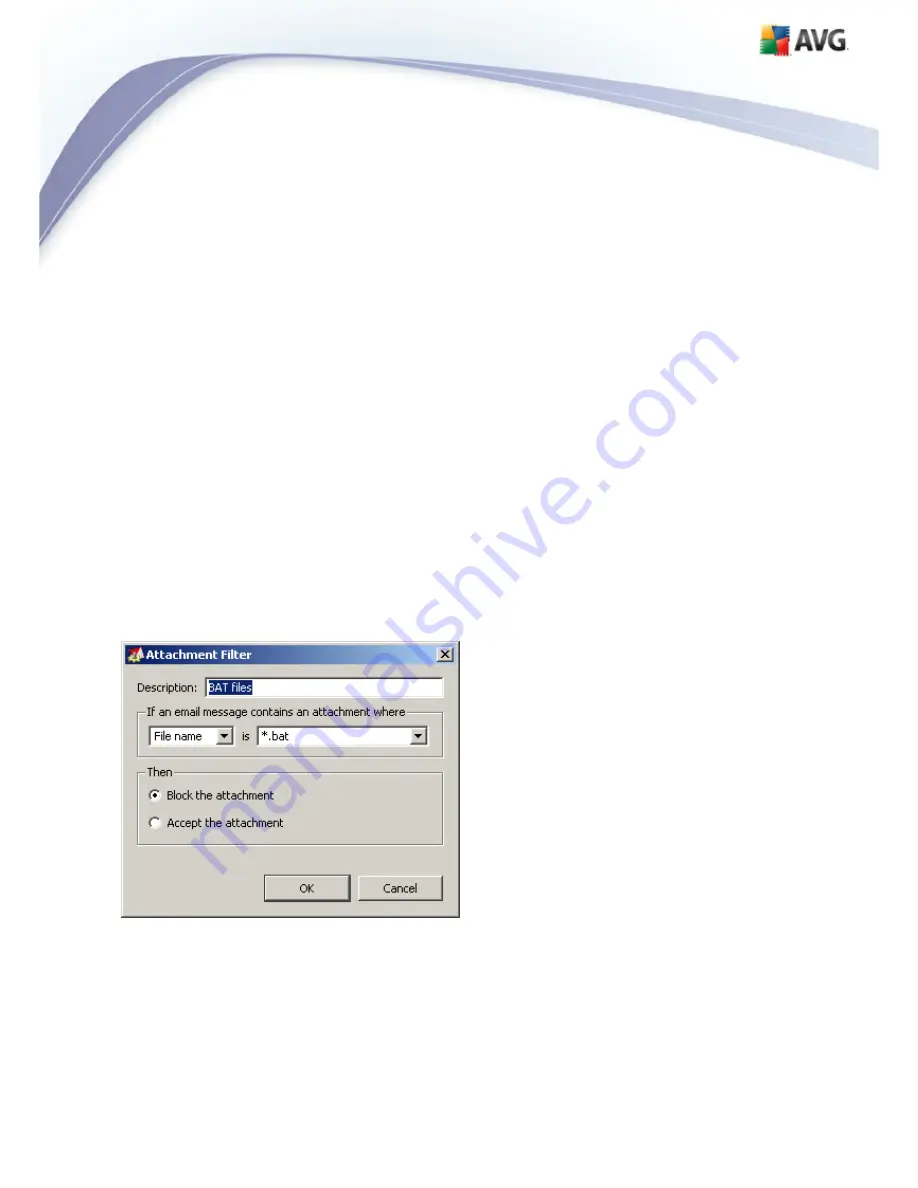
In the list of extensions, each item has four fields:
·
Type
– specification of the kind of attachment determined by the extension
given in the Content field. Possible types are File name or MIME type. You can
select the respective box in this field to include/exclude the item from
attachment filtering.
·
Content
– an extension to be filtered can be specified here. You can use
operation system wildcards here (for example the string ‘*.doc.*’ stands for any
file with the .doc extension, and any other extension following).
·
Action
– define action to be performed with the particular attachment. Possible
actions are Accept (accept the attachment), and Block (block the attachment
as defined in the Action tab dialog).
·
Description
– description of the attachment is defined in this field.
An item is removed from the list by pressing the Remove button. You can add another
item to the list by pressing the
Add…
button. Or, you can edit an existing record by
pressing the
Edit…
button. The following window then appears:
·
In the Description field you can write a short description of the attachment to be