A V G 9 I nternet Sec urity © 2 0 1 0 C opyright A V G T ec hnologies C Z, s .r.o. A ll rights res erved.
5 8
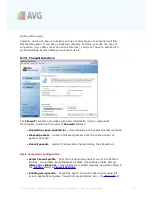
Basic component configuration
In the bottom part of the dialog you will find the
Identity Protection settings
section
where you can edit some elementary features of the component's functionality:
·
Identity Protection is active
- (
on by default
): check to activate the IDP
component, and to open further editing options.
In some cases,
Identity Protection
may report that some legitimate file is
suspicious or dangerous. Since
Identity Protection
detects threats based on
their behavior, this usually occurs when some program tries to monitor key
presses, install other programs or a new driver is installed on the computer.
Therefore please select one of the following options specifying
Identity
Protection
component's behavior in case of a suspicious activity detection:
o
Always prompt
- if an application is detected as malware, you will be
asked whether it should be blocked (
this option is on by default and it is
recommended not to change it unless you have a real reason to do so
)
o
Automatically quarantine detected threats
- all applications detected
as malware will be blocked automatically
o
Automatically quarantine known threats
- only those applications that
are with absolute certainty detected as malware will be blocked
Control buttons