A V G 9 I nternet Sec urity © 2 0 1 0 C opyright A V G T ec hnologies C Z, s .r.o. A ll rights res erved.
8 0
9.1.9. E-mail Notifier
The
E-mail Notifier
button allows you to activate the option of being informed about
newly arrived e-mail messages directly in the
AVG Security Toolbar
interface. The
button opens the following editing dialog where you can define parameters of your e-
mail account and the e-mail display rules. Please follow the instructions in the dialog:
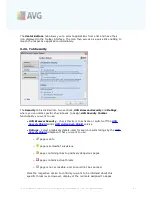
·
Account type
- Specify the protocol type your e-mail account uses. You can
select among the following alternatives:
Gmail
,
POP3
, or select the server
name from the drop down menu within the
Other
item (
at the moment, you
can use this option if your account is on Yahoo! Mail or Hotmail
). If you are
not sure what e-mail server type your account uses, try to find the information
from your e-mail provider, or your internet service provider.
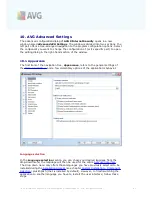
·
Login
- In the login section provide the exact form of the user name to your
e-mail account, and the respective password. Further, provide the name of the
incoming mail server, and specify the port number if needed. Again, if needed,
you should be able to gain this information from your e-mail provider, or your
internet service provider.
·
Check for new e-mails every ... minutes
- Define the time interval to be
used to check for new e-mail messages (
in the range of 5-120 minutes
), and
specify whether and how you want to be informed about the new message
arrival.