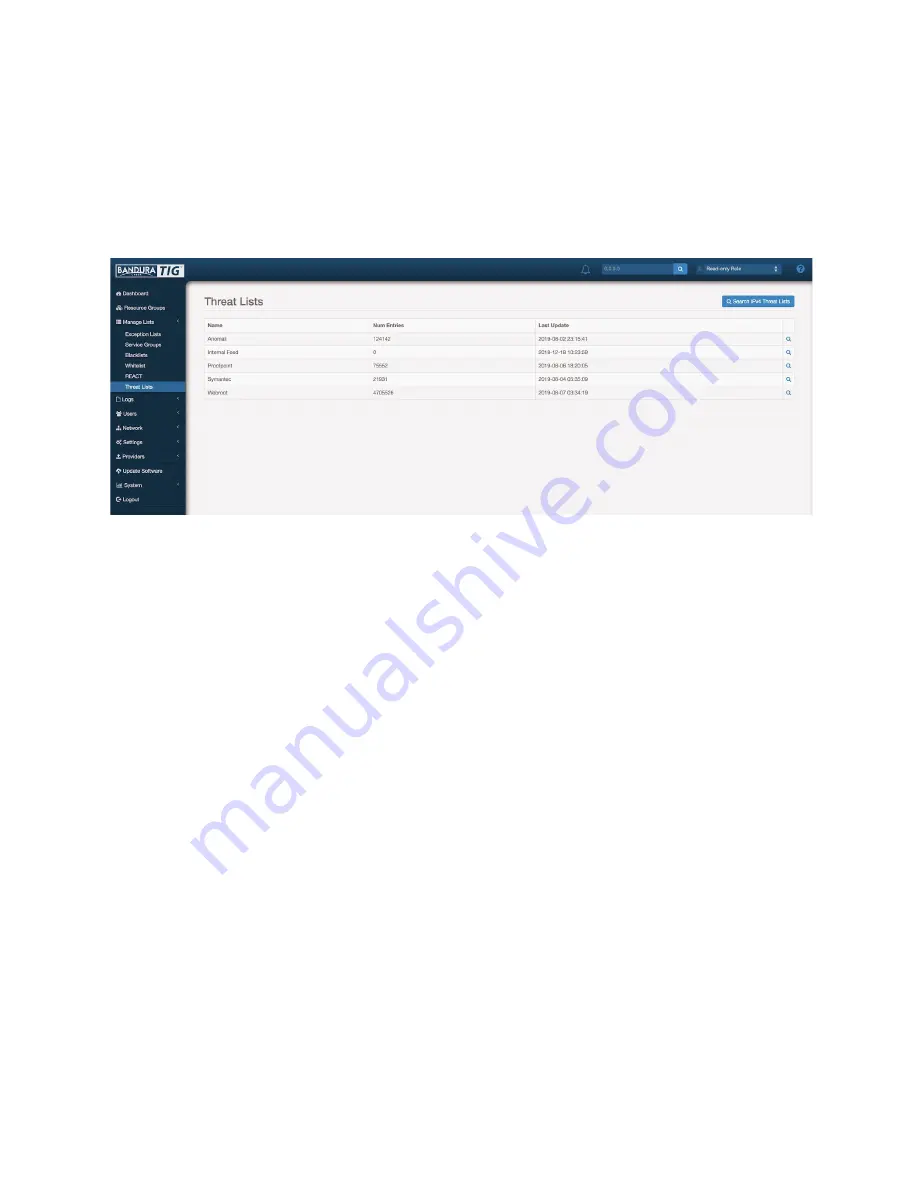
3.3.6 Threat Lists
A threat intelligence feed is an ongoing stream of data related to potential or current threats to
an organization's security. Threat intelligence data feeds provide users with constantly updated
information about potential sources of attack. Webroot is available by default, or Symantec and
ProofPoint can be added as an additional cost.
3.4 Logs
The Bandura Cyber TIG keeps log files of inbound/outbound traffic and system events. You can
browse these log files and send the data to external syslog servers. You can also set up alarms
to notify you if any of these files become filled.
3.4.1 Connections
The
Connections Log
shows information of data packets being filtered by the Bandura Cyber
TIG. The Connections Log will tell you the following information of the packets:
● Date and Time
● Country
● ASN
● Source IP
● Destination IP
● Inbound or Outbound
● Blocked or Allowed
● Risk Category
● Reason for being allowed or denied
● Resource Group that allowed or denied the connection
Filter your results for a more precise search or export the logs via CSV or PDF.
40









































